What is Azure AD connect, and how is it related to Intune?
If you are familiar with the concept of Windows Server Active Directory, then you already have a good idea of what Azure AD is. It essentially is a cloud version of Active Directory which was introduced in Server 2000, which seems like forever ago. In technical terms, it is Microsoft’s cloud-based identity and access management service. The basic concept of the two AD’s is the same; users logon and authenticated to AD and then access resources.
So why the need for Azure AD? Well, we live in a different world today than we did when Server 2000 was unveiled. We live in a mobile age that is dominated by the Internet and traditional AD wasn’t designed for a world like that. Azure AD on the other hand is designed to support web-based services that use Representational State Transfer API interfaces. In simple terms, it was created for cloud based applications such as Office 365, Salesforce.com, etc. To do that, it had to be based on completely different protocols, specifically SAML and OAuth 2.0.
There are a number of versions of Azure AD:
- Azure Active Directory Free
- Azure Active Directory Basic
- Azure Active Directory Premium P1
- Azure Active Directory Premium P2
The differences between these different versions is two fold. As you move up from the free version, you get more features, which of course, you guessed it, costs more money. Except for Azure Active Directory Free, which is complimentary if you have a paid subscription to Office 365, Microsoft Dynamics CRM Online, Enterprise Mobility Suite, or other Microsoft services, the other versions require some sort of subscription free that goes up along with the number of feature packages.
There are several integral components of Azure AD. They are:
- Azure AD Directory – the equivalent to the domain of Windows Server AD, it is what contains the tenant’s users, groups, apps, devices, etc.
- Azure AD Account – an identity created through Azure AD or another Microsoft cloud service such as Office 365.
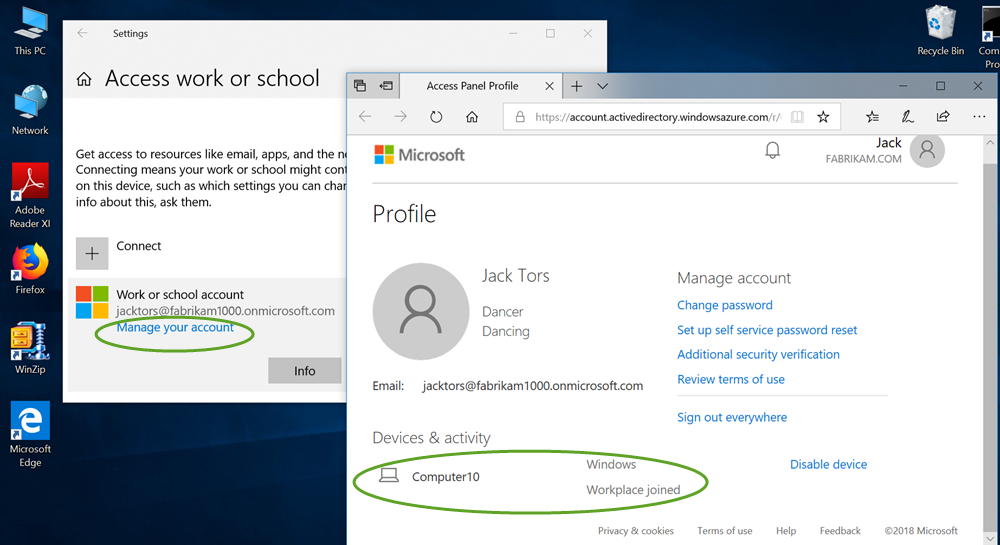
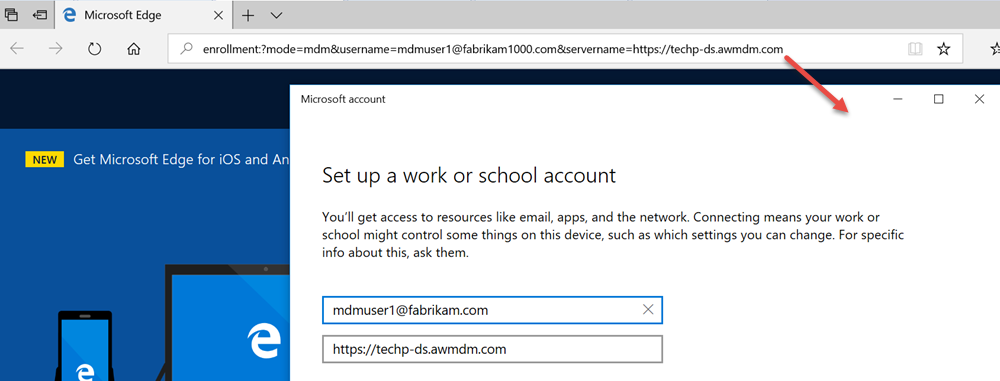
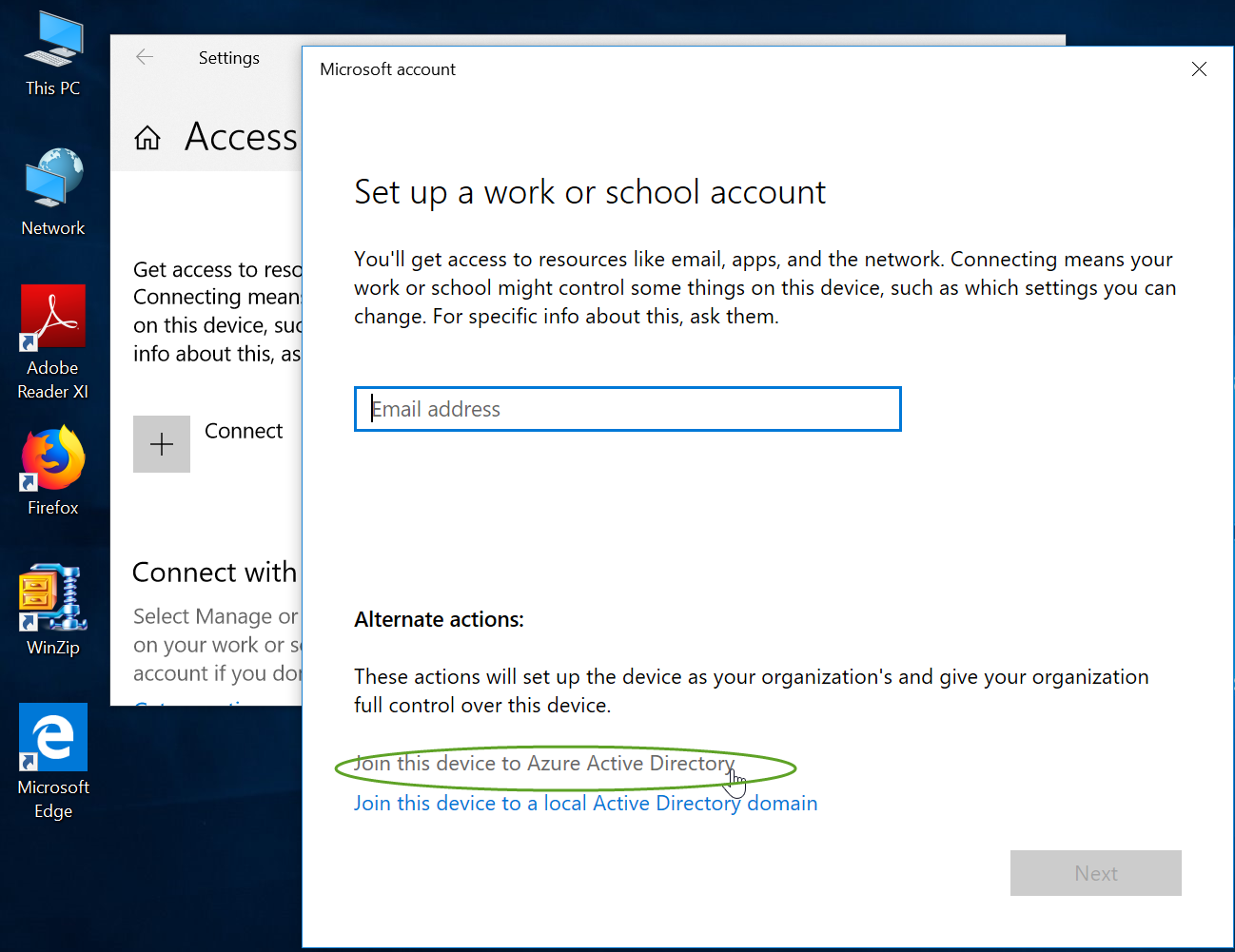
The Azure AD account gives users access to their organization’s cloud service subscriptions. On a Windows 10 device, it is referred to as a Work or School Account. The screenshot below illustrates how one would manually join a Windows 10 device to Azure AD.
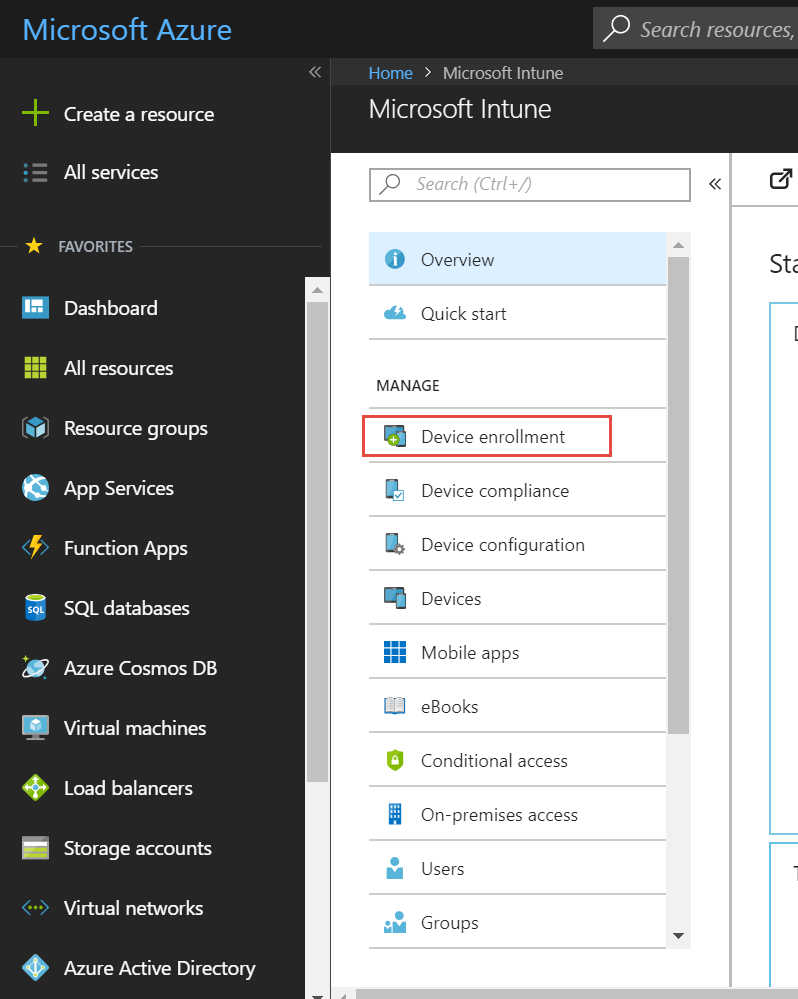
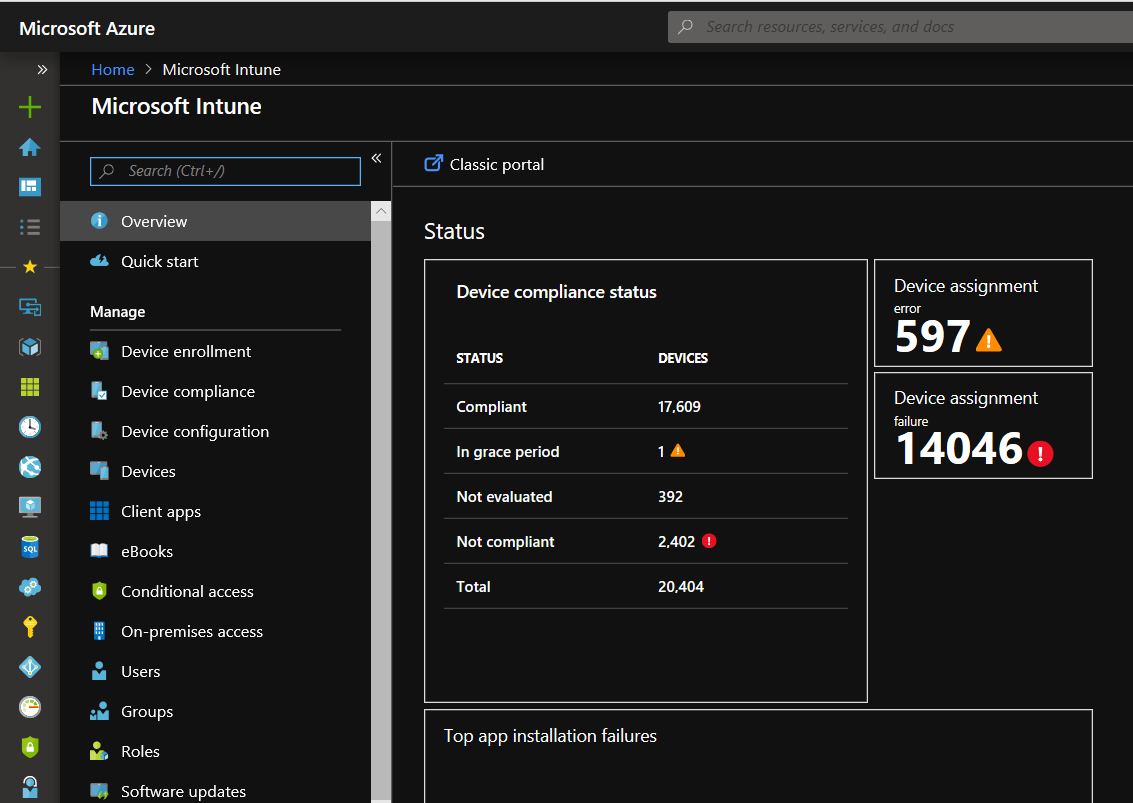
Azure AD is highly scalable. Even the free version can contain 500,000 objects. With so many users, accounts and applications, an organization undoubtedly needs one or more administrators to manage everything. Below is the management screen of Azure AD.
So how does Azure AD relate to Intune?
Well, the two work hand-in-hand.
In practivcal terms, you really cannot have Intune with Azure AD.
In the same way that Windows Group Policy helped deliver and manage settings for Windows domain join machines, Intune is the mobile device management tool that integrates with Azure AD in order to manage settings as well. It also protects your organization’s resources by controlling how users can access and share it and can lock down devices that may have been stolen or compromised.