The Many Ways to Configure Windows Firewall Rules using Intune or Command Line
The Many Ways to Configure Windows Firewall Rules
In today's rapidly evolving threat landscape, organizations must prioritize a multilayer security strategy. That includes configuring and enforcing Windows Firewall on servers and workstations. In this article we will look at the multiple ways to deliver Windows Firewall settings to your Windows devices.
Using Intune
There are a several ways to configure Windows Firewall Rules and enforce them using the Microsoft Intune Admin Center. One way is to navigate to Endpoint Security > Firewall and click “Create Policy.” Then choose “Windows” as the Platform and then choose one of the two Profile options:
Windows Firewall: Choose this option to enable or disable the Windows Firewall for different network profiles and only need basic firewall settings and configurations.
Windows Firewall Rules: Use this option if you already have Windows Firewall enabled and you want to create granular custom firewall rules for inbound and outbound traffic.
In the example below I chose Windows Firewall.
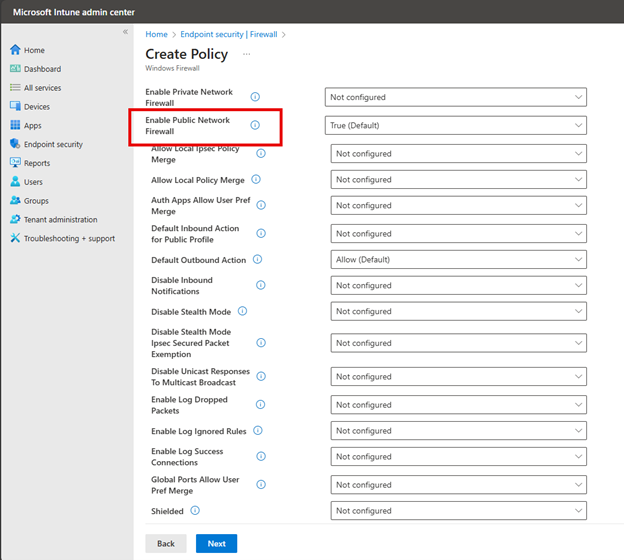
You then have the option to enable or disable the Windows Firewall for Domain, Private or Public Networks. If you aren’t sure which profile to choose, here are some tips:
- The Domain profile in Windows Firewall is applied when a computer is connected to a network that is identified as a Domain Network. The Domain profile takes precedence over Private and Public profiles when connected to a domain network and is typically more permissive than the Public profile, as the domain network is assumed to be trusted and secure.
- The Network private profile is for networks in which devices are visible to one another on the same network. Network discovery is usually enabled and file and printer sharing features are active. This profile is typically used for SOHO environments.
- The Public profile is designed for use on untrusted networks such as an establishment that provides a public or guest network. The devices are not discoverable by other devices on the network stricter firewall rules are applied to limit incoming connections.
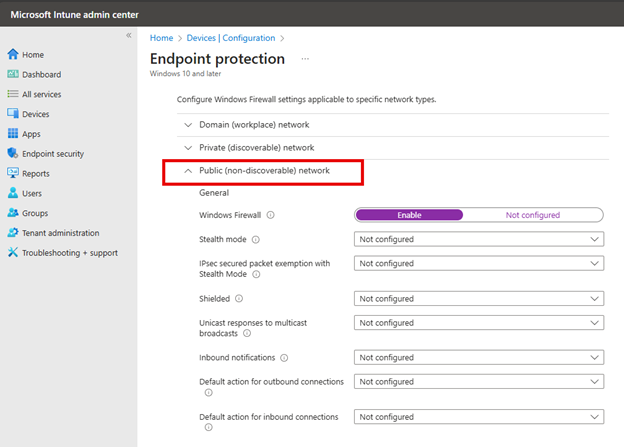
You can then configure basic settings for each of these profiles as shown below. Here I chose to enable the Public Network.
Choosing the Windows Firewall Rules option I outlined earlier provides you with a different interface to select more customized rules as shown in the screenshot below.
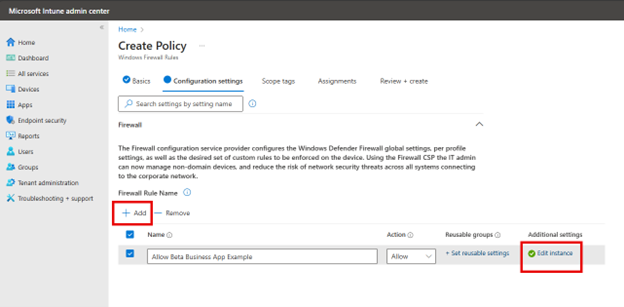
Clicking the Edit instance will prompt you with the port configuration settings.
You can also configure Windows Firewall using Intune Configuration profiles. Navigate to Devices > Configuration Profiles and create a new profile. Select Windows 10 and later as the platform. Then choose Endpoint protection as the profile type as shown below.
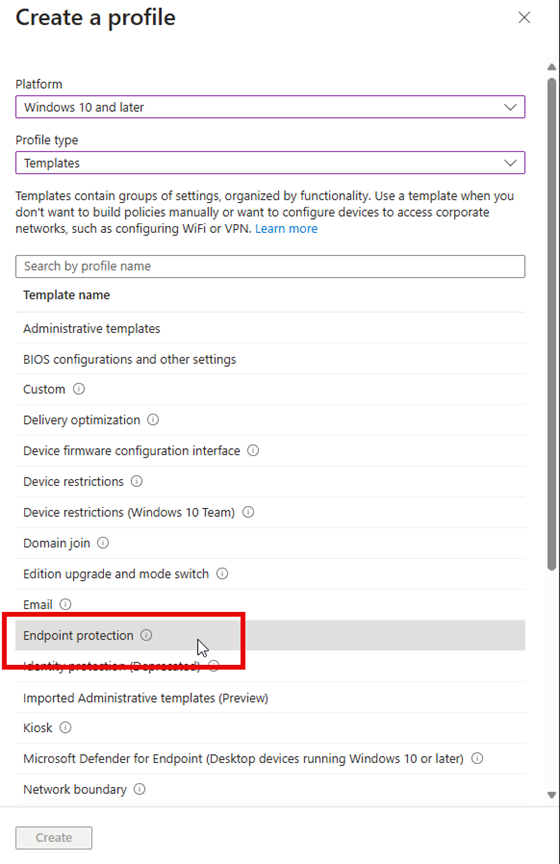
Name the profile and then proceed to the next screen where once again, you can configure basic settings for the Domain, Private and Public profiles.
Another approach to configuring firewall rules with Intune is to use PowerShell Script Deployment. This method leverages NetFirewallRule cmdlets to define firewall rules as is shown below:
New-NetFirewallRule -DisplayName "Allow Inbound Port 80" -Direction Inbound -LocalPort 80 -Protocol TCP -Action Allow
You would then use the Microsoft Win32 Content Prep Tool and package it into an .intunewin file. You can download the Win32 Content Prep Tool from Microsoft's official GitHub repository. Then go to the Microsoft Intune Admin Center and navigate to Apps > Windows > and add a new Windows app (Win32). Then upload the .intunewin file and set the following install command:
powershell.exe -executionpolicy bypass -file
Whichever option you choose to deliver the Firewall settings, you would then assign the profile to the designated groups you want to target and then save it.
Using Group Policy
If you want to configure Firewall settings for domain-joined computers, then Group Policy is the best option. Using the Group Policy Management Console, create a new GPO and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Windows Defender Firewall with Advanced Security. You can enable your desired network profiles by right-clicking on "Windows Defender Firewall with Advanced Security" and selecting "Properties.” To add rules, you would expand either "Inbound Rules" or "Outbound Rules" and right-click and select "New Rule.” Then simply follow the wizard to define the ports, programs or custom rules you want as shown below.
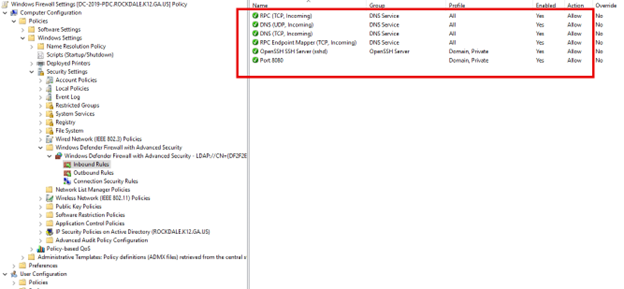
Ultimately, whether using Intune or Group Policy, the goal remains the same: to protect critical assets from unauthorized access and potential threats while maintaining seamless operational efficiency. Stay safe out there.




Comments (0)