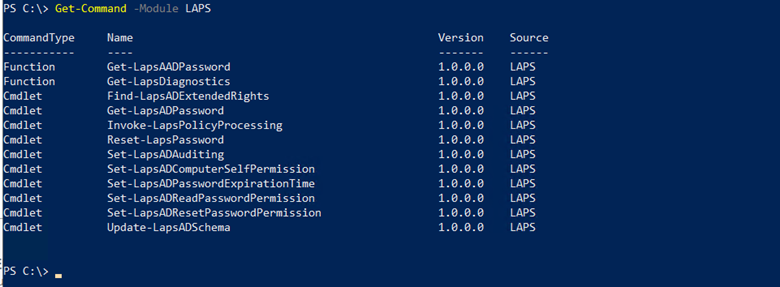
What is Legacy Microsoft LAPS Emulation Mode?
In my two previous blogs I outlined the improved features and capabilities of the latest version of LAPS that was introduced made available with the Windows Update released on April 11, 2023. The new version called Windows LAPS (that I refer to as LAPS2), addressed some of the limitations of the original version called Legacy LAPS (or LAPS1). Those who have relied on LAPS1 will certainly want to upgrade to the newest version but what happens when you bring LAPS2 into a LAPS1 environment? The short answer is that you cannot run both versions of LAPS on the same machine simultaneously. Any settings that are singular to one LAPS version are not accessible in the other one and vice versa.
When you bring LAPS2 into an environment that has preexisting instances of LAPS1 you have two options. Either delete all instances of LAPS1 before implementing LAPS2 or use legacy Microsoft LAPS emulation mode to accommodate both to some degree.
Legacy Microsoft LAPS Emulation Mode Limitations
The original LAPS was implemented by installing the Microsoft LAPS Group Policy Client Side Extension. It is that extension that retrieves the LAPS password information from AD and stores it in the computer’s local security database. You can detect whether a computer has the installed extension by looking for the following registry key:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions\{D76B9641-3288-4f75-942D-087DE603E3EA}
Once you deploy LAPS2 to a machine already running LAPS1, that computer is running in emulation mode. Legacy Microsoft LAPS emulation mode prevents both LAPS from running simultaneously as this would create a security risk. That means that while the computer has LAPS2 installed, it is still restricted to some of the limitations of LAPS1. This means that:
- You can only store passwords to local AD as only LAPS2 supports Azure AD and local AD.
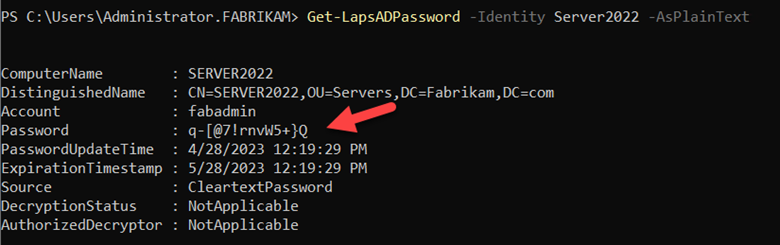
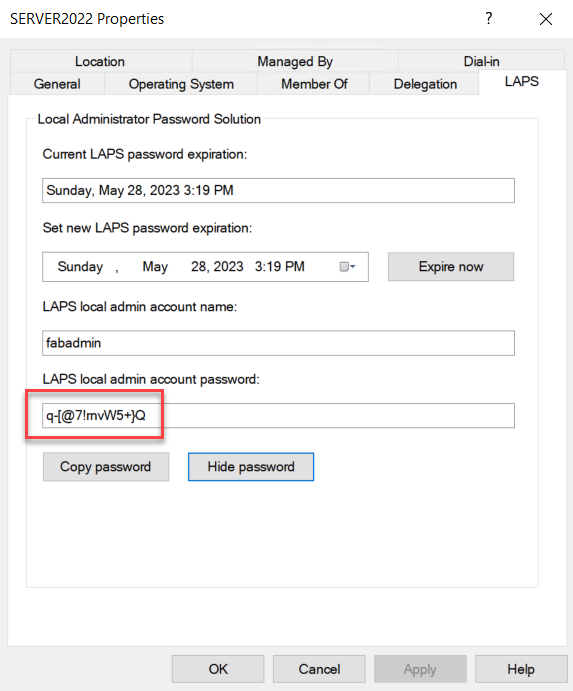
- Passwords will be stored in clear-text form. LAPS1 does not support password encryption so while the newest version of LAPS does, you cannot take advantage of it.
- The Windows Server Active Directory Users and Computer management console doesn't support reading or writing legacy Microsoft LAPS schema attributes.
- You will not be able to use some of the newer LAPS2 scripts. For instance, cannot you use the
Set-LapsADPasswordExpirationTime cmdlet to modify the existing legacy LAPS password expiration attribute.
- All Windows LAPS policy knobs that aren't supported by legacy Microsoft LAPS will default to their disabled or default settings.
Note that if you try to install LAPS1 on a machine that already has LAPS2, LAPS1 will be ignored. In other words, whichever version of LAPS is installed first takes precedence over the other.
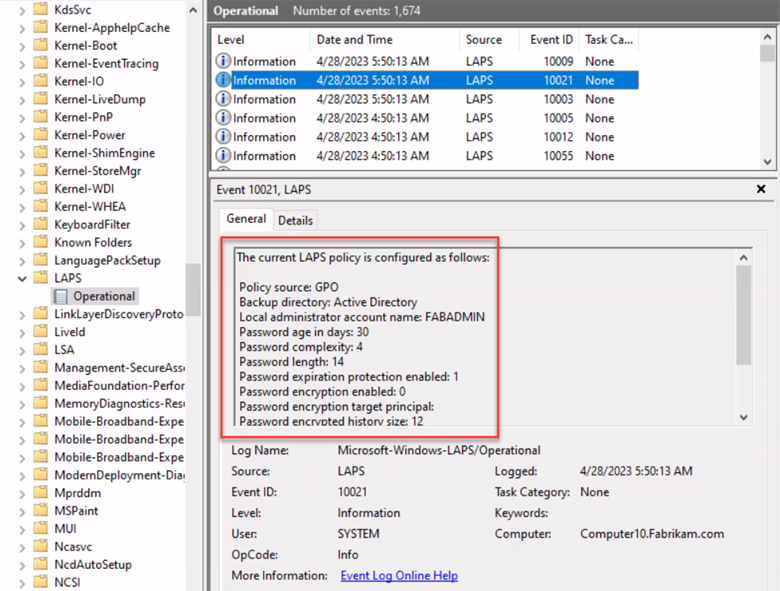
You can tell if a computer is in emulation mode by going to Event Viewer and navigating to Application and Service Logs > Microsoft > Windows > LAPS > Operational and look for the 10023 event which will show Legacy LAPS as the policy source.
Switching from Emulation Mode
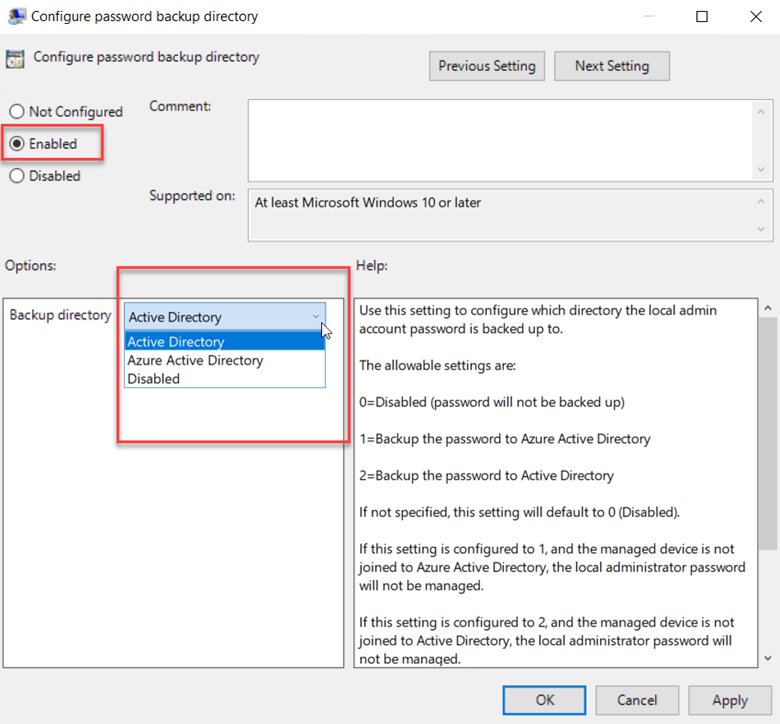
Once you have implemented LAPS2, you will want to eventually move on from emulation mode. You can disable Microsoft LAPS emulation mode by creating a REG_DWORD registry value named BackupDirectory under the:
HKLM\Software\Microsoft\Windows\CurrentVersion\LAPS\Config key
and set it to the value of zero. This will prevent LAPS2 from entering legacy Microsoft LAPS emulation mode regardless of whether the Windows LAPS CSE is installed or not.
Remember that the new Windows LAPS does not require you to install any type of CSE. Once a computer receives the April 2023 update and is joined to either Azure or Azure AD, it is LAPS2 capable. After that it just needs the LAPS policy to deliver the configured settings.