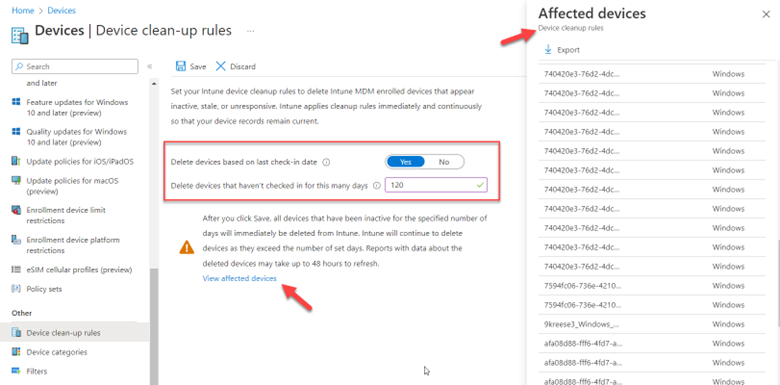
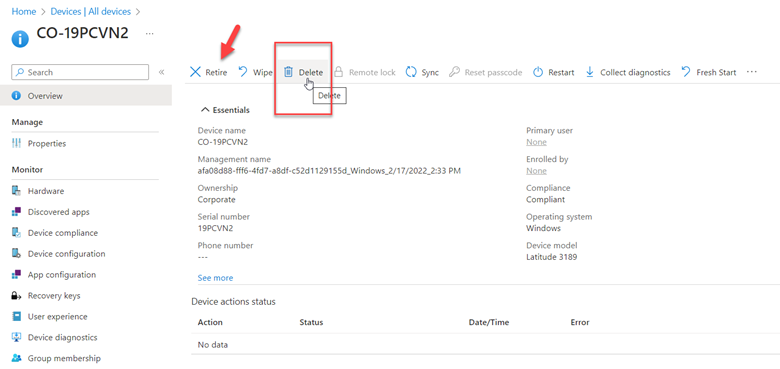
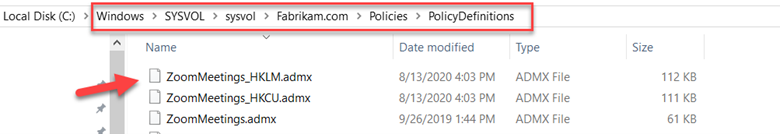
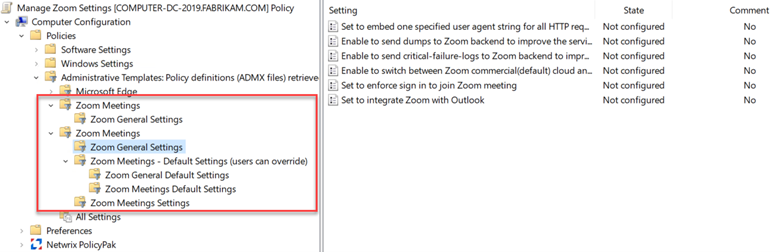
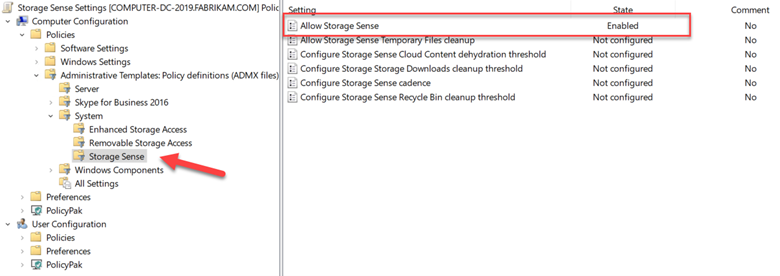
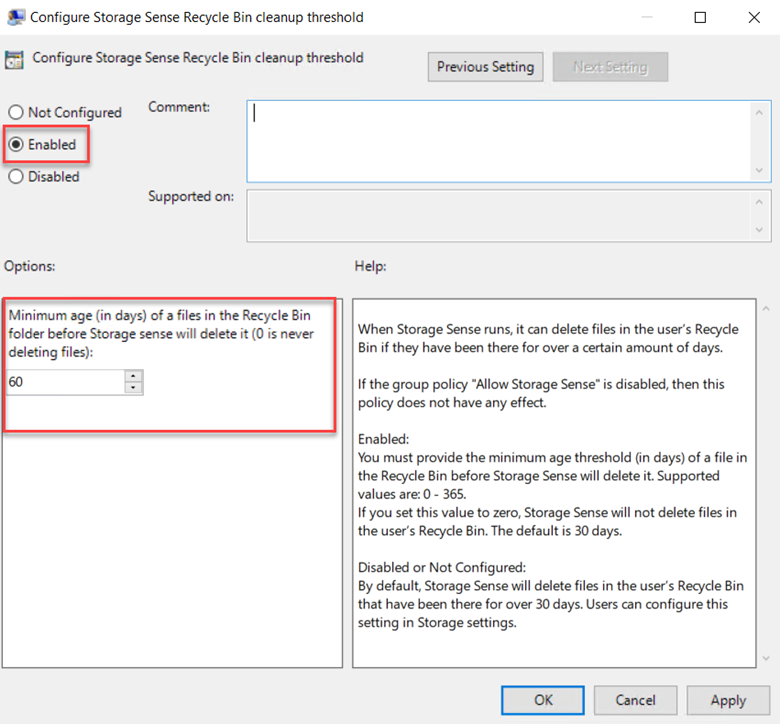
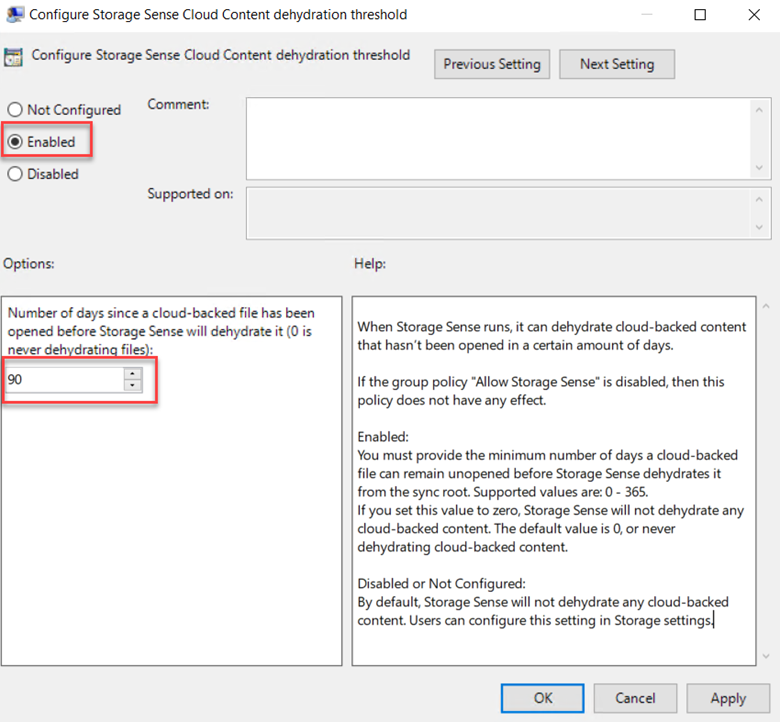
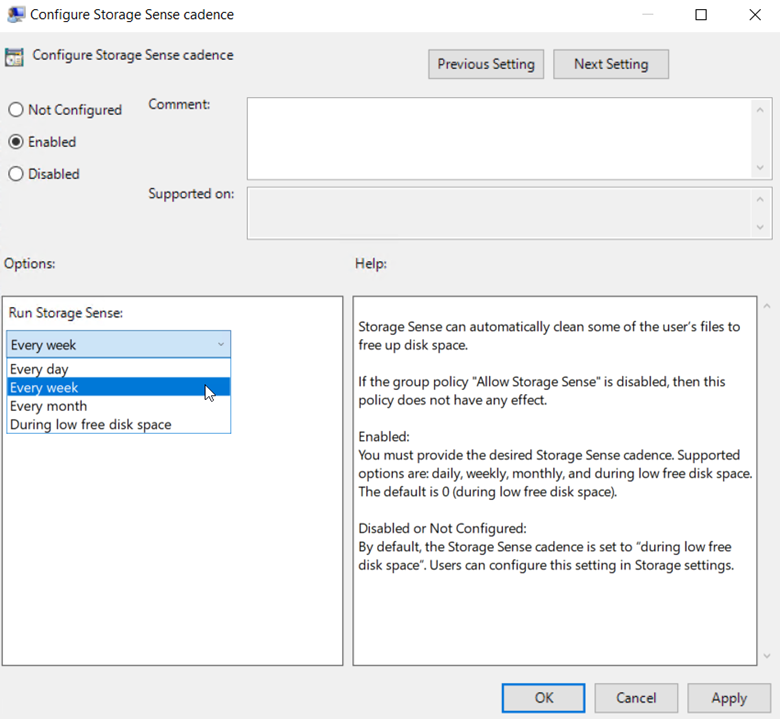
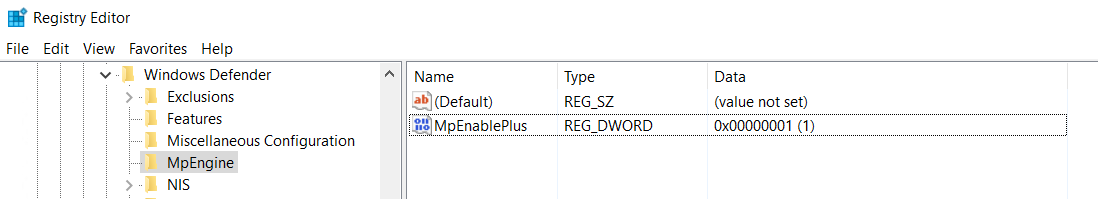
Intune has come a long way since its inception and now offers a lot of great features to manage your organization’s mobile and Windows 10 devices. The MDM approach to device management is a real change from years ago in which computing devices were either managed through the traditional AD joined domain model or were simply allowed to operate independently at the discretion of the user.
Intune continues to introduce cloud based services that streamline and secure your devices, but users are often slow to accept changes into their environment. In order to better educate users about the importance and need for device management and mobile security, Microsoft just recently updated the Intune Customer Adaption Pack in order to make the change in approach more palatable and decrease the transition time of Intune enrollment. The adaption pack is especially valuable to organizations that previously did not require mobile devices to be enrolled for work access.
What’s in the Intune Customer Adaption Pack
The Adaption Pack is essentially a comprehensive communication plan that sets out to accomplish three objectives:
- Education users in how to enroll their particular devices in Intune
- Reassure users about their privacy concerning what type of device data is shared with IT
- Explains the safeguards in place to protect user privacy and company resources
The adaption kit is suited for IT admins, management and trainers to educate, prepare and guide their users for the enrollment process.
You can download the Intune Adaption Pack here.
IT admins, management, and trainers
The link downloads a zip file that includes a variety of documents, videos, posters and templates that can be leveraged to spread Intune adaption throughout your organization. The enclosed contents are shown in the screenshot below.
The Welcome document outlines what is in the adaption kit. The kit includes two email templates that can be used to communicate with your users about the coming transition to Intune. You can use them as written or customize them according to your needs. An example of email #1 is shown below.

As part of the , all employees worldwide will soon transition to Microsoft Intune, a unified mobile device management platform. Intune enables you to work productively and securely from anywhere, at any time and across all of your devices. All other mobile device management platforms used worldwide to secure documents, devices, and corporate data will be retired.
The email goes on to explain some of the benefits and expectations of Intune as well as a schedule of the coming steps that they will be asked to complete at the appropriate time. This opening email also provides an opportunity to showcase any other new services whose access will be granted on devices managed by Intune. These required actions are then outlined in the second email template that also reinforces the benefits and strategic reasons for the migration and provides users a timeline for the outlined process.
The Intune Deployment Guide provides a wealth of information for your users that is compressed into two palatable pages that they can quickly read and apprehend. The guide also includes a Word version that allows you to customize and include your internal resources and contact information. Some of the topics outlined include:
- What information about their personal devices can and cannot be seen by IT? This includes a link to the Intune privacy policy.
- How internal IT will use the company portal or app store to install work apps
- What users can do if their mobile device is lost or stolen
- Security steps IT can take to secure data residing on enrolled devices
- Intune enrollment links for each applicable operating system
An example of the guide is shown below.

Training Videos
If you’ve had concerns about how to train your users to complete the enrollment process, the enclosed videos in the Adaption Pack will be a welcome tool. The videos are step-by-step YouTube videos that show users how to easily enroll their devices in Intune. Below is a screenshot of the Windows 10 video.
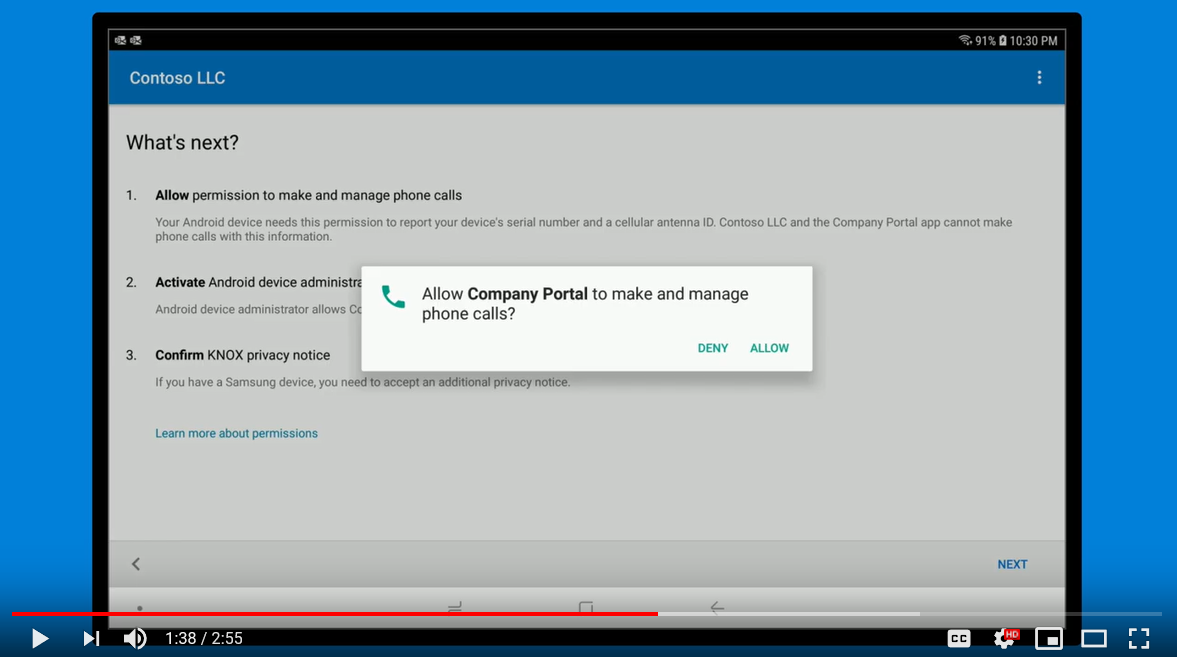
Two videos demonstrate how to either enroll an Android device for full management or enroll for Work Profile management. An example of the Android device management is shown below.
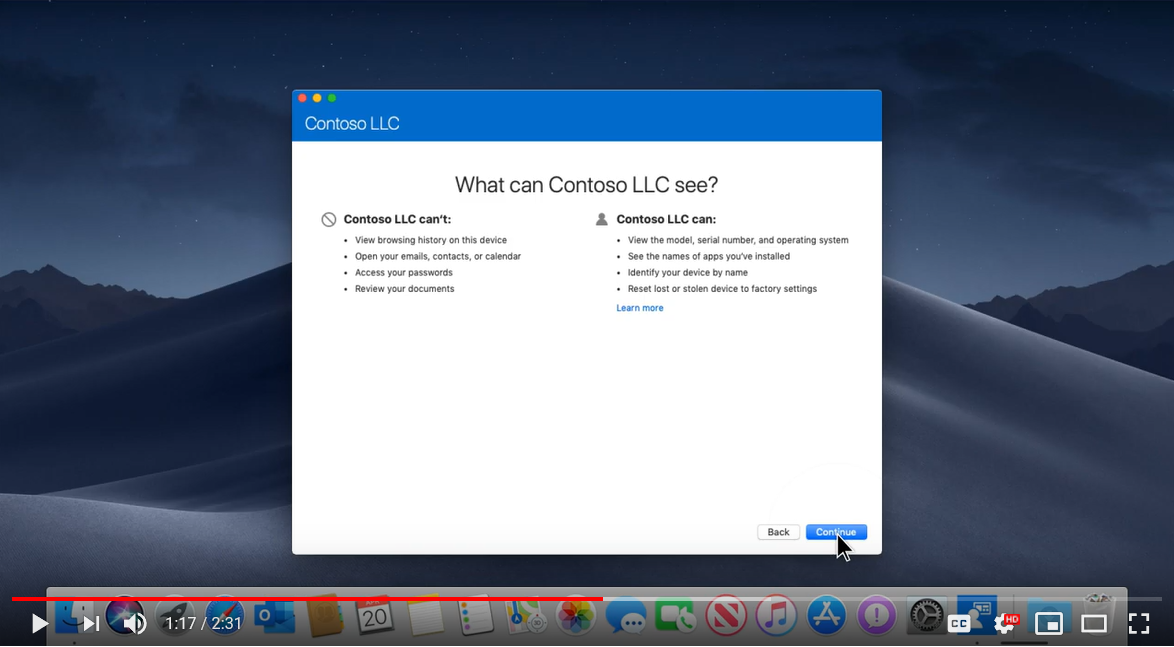
The videos not only provide step-by-step directions on how to complete the enrollment process, but also summarizes again what information Intune has access to when it comes to user devices. An example of this is shown in the MacOS video. Note that there is also a separate video concerning iOS devices as well.
A Great Tool to Assure a Smooth Transition
The Intune Customer Adaption Kit gives you out-of-the-box training tools to educate your users about why Intune enrollment is so important. It can help ensure that all targeted devices are enrolled quickly without the constant prodding of your users asking “what to do.” By effectively communicating the necessary messages and information to your users, you will be able to begin enforcing compliance through conditional policies for all of your targeted devices.