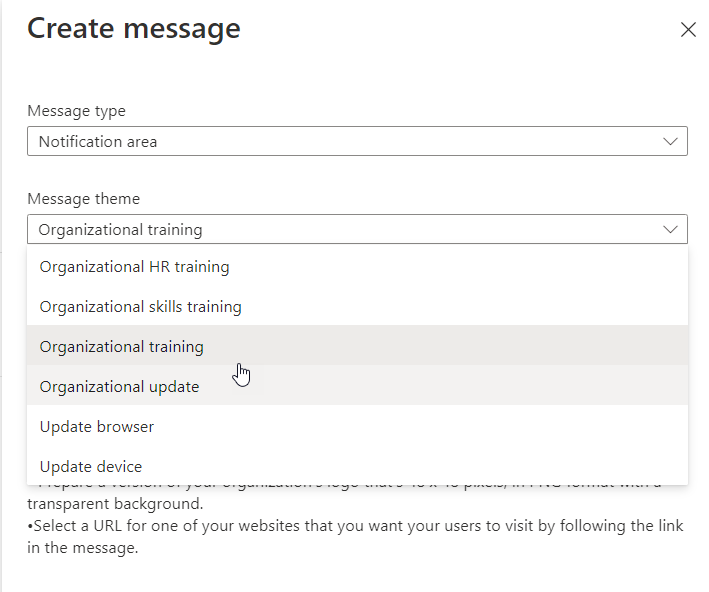
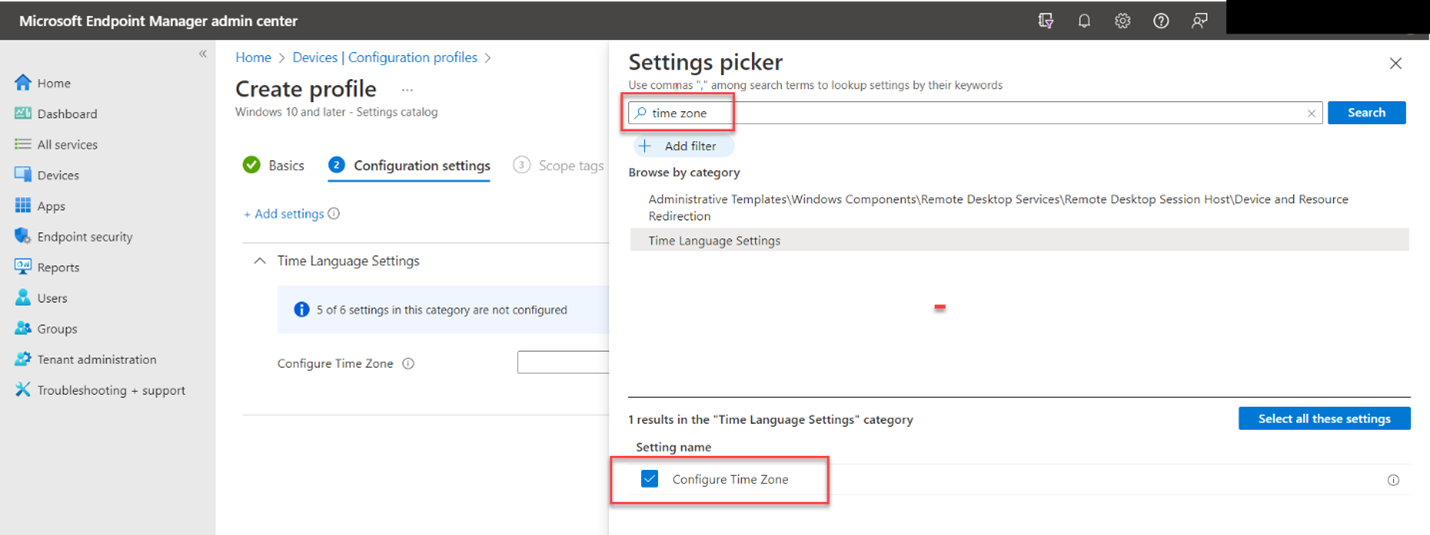
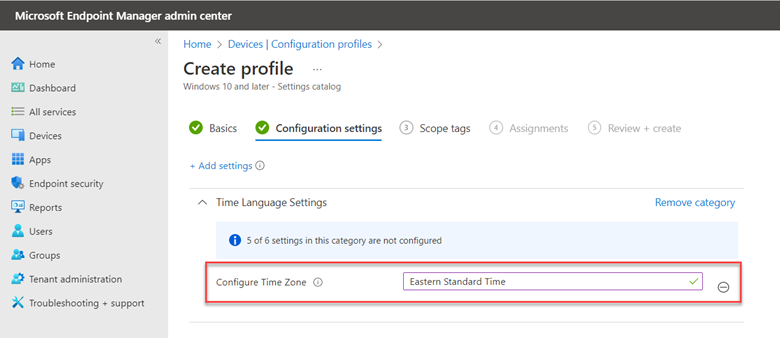
How to Make a Basic Edge Browser Policy using Group Policy or Intune
From websites to email and SaaS applications, the web browser is now the go-to app for your users. Optimizing the user digital experience often starts with optimizing their browser environment. Whether you implement Group Policy or Intune, you need to create a policy for your organization’s preferred browser, and we are going to do just that. I have chosen Edge because it is generally easier to secure with these two management tools. There are so many settings in Edge that GP and Intune can manage. We are just going to outline some of the basics that serve as a good start.
Enforce Bing and Google SafeSearch
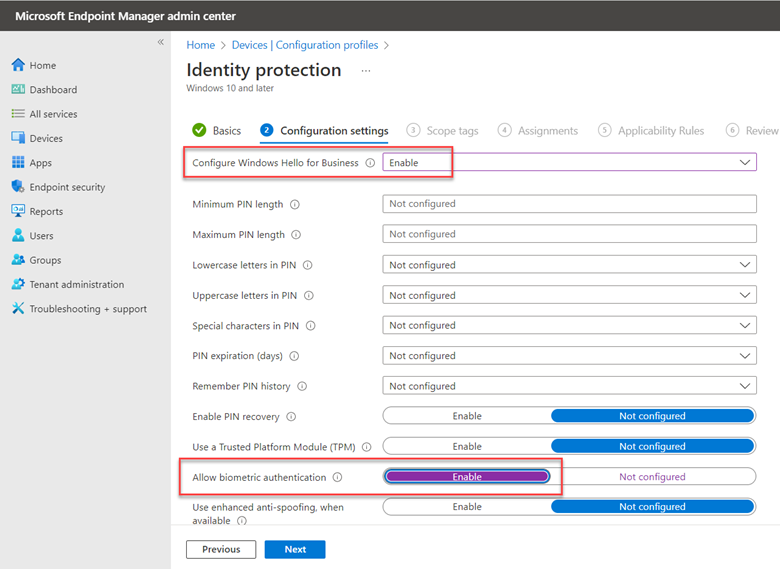
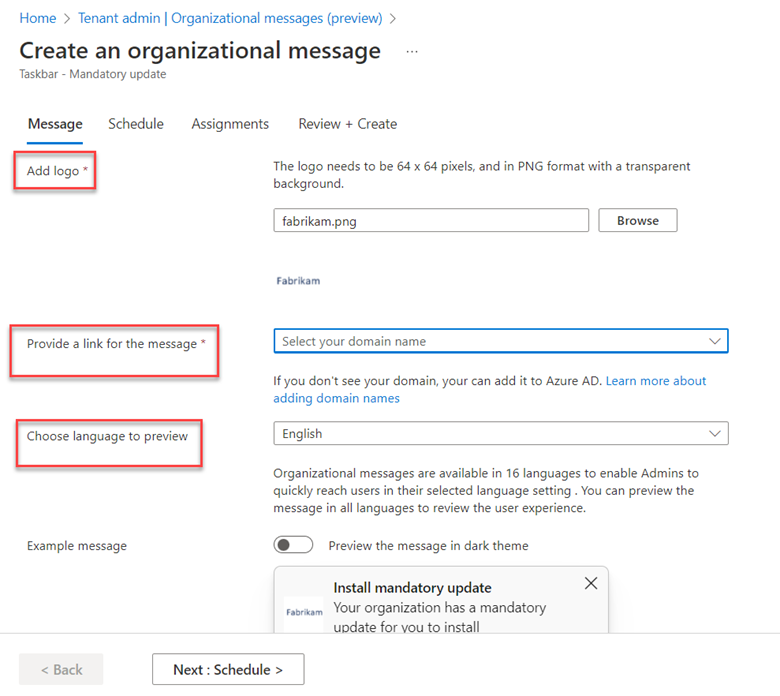
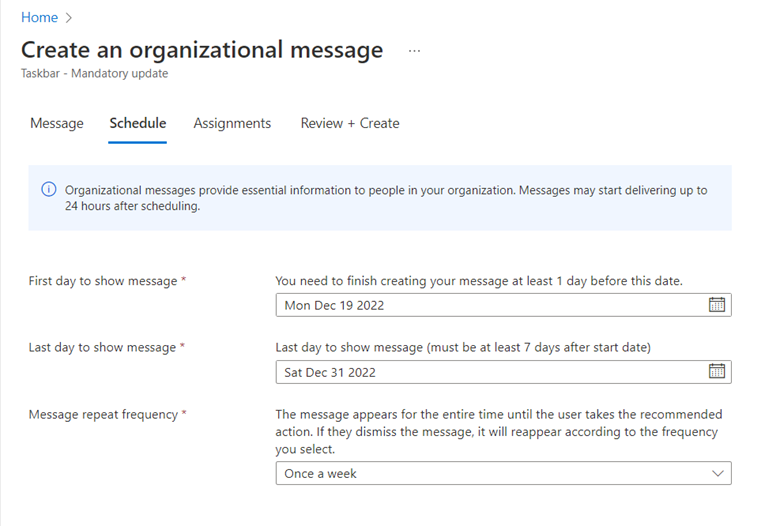
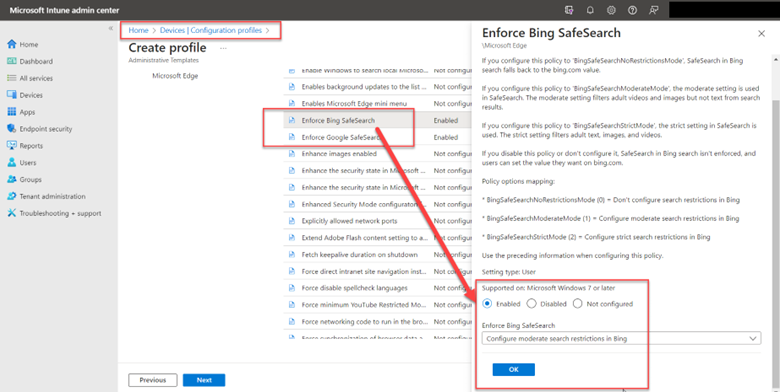
Most organizations want to filter out explicit or inappropriate content from search results. If you don’t have an enterprise web filter or just want to create a backup policy in case your filter goes down, you can enforce Bing SafeSearch and Google SafeSearch. For Intune, go to Devices > Configuration profiles > Create profile. Select Windows 10 and later as the platform and Templates > Administrative Templates as the Profile type. Then go to User Configuration > Microsoft Edge and find the settings “Enforce Bing SafeSearch” and “Enforce Google SafeSearch.” In the example below I chose moderate search restrictions which will filter adult images and videos but not text.
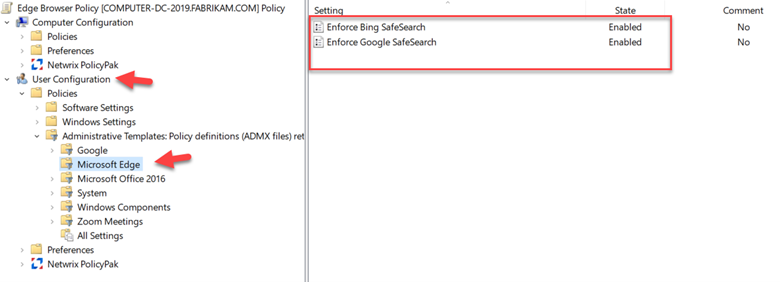
You can do the same using Group Policy by following the same Administrative Template path as shown in the screenshot below.
Restrict Access to Developer Tools
In our previous example, you had to sift through multiple pages of settings until you could access the Enforce SafeSearch settings. For instance, the first page of settings for Microsoft Edge only contains two settings as shown here.
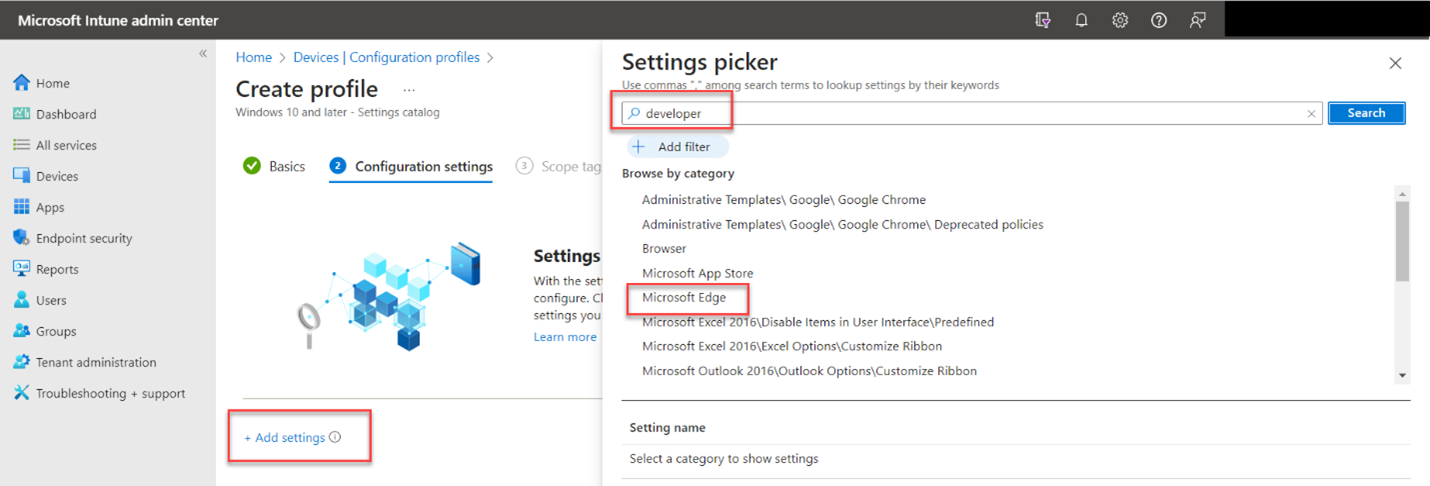
This time we will restrict user access to the developer tools in the Edge browser. To make it easier to find the desired setting, let’s use the Settings catalog for the profile type rather than the Administrative templates. Using the Settings Catalog, do a search for the word “developer” and then click on Microsoft Edge in the results as shown below.
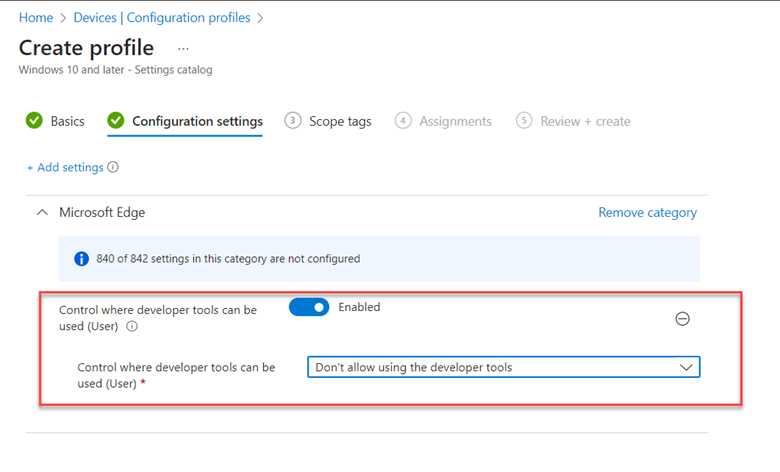
Then enable the “Control where developer tools can be used (User) and select “Don’t allow using the developer tools” in the drop-down menu as I have done in the example below.
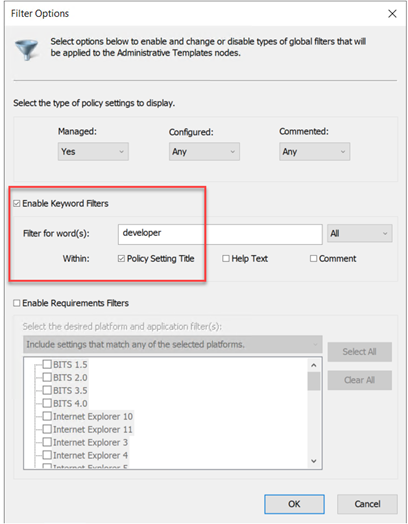
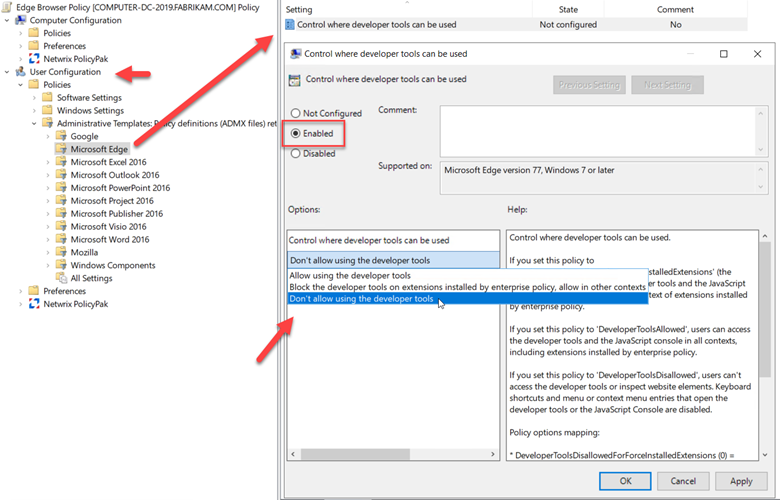
In Group Policy, you can use the Filter to quickly find the exact setting you need. Simply filter the word developer as shown in the screenshot below.
Then navigate to User Configuration > Microsoft Edge and configure the “Control where developer tools can be used” setting as shown in the screenshot below.
Managing Installed Web Extensions
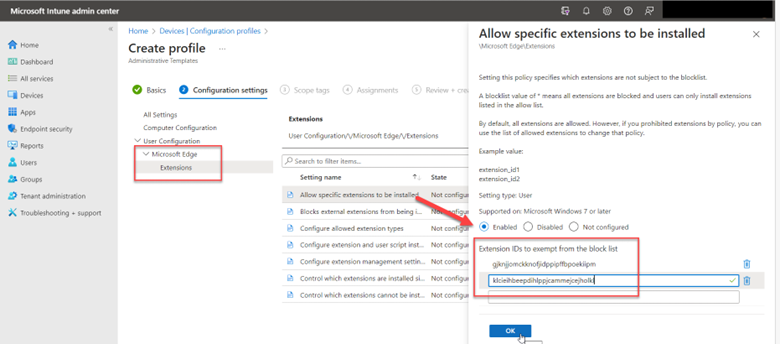
You want to have control over what browser extensions your users will have. Let’s start with which extensions will be allowed. Using Intune, use Administrative Templates once again as your profile type and navigate to Microsoft Edge > Extensions and enable “Allow specific extensions to be installed.” You will then have to input the ID for each web extension. I the example below I have added the ID for Microsoft Translator (gjknjjomckknofjidppipffbpoekiipm), followed by Adobe Acrobat (klcieihbeepdihlppjcammejcejholkl). Note that the extension IDs are different for each web browser.
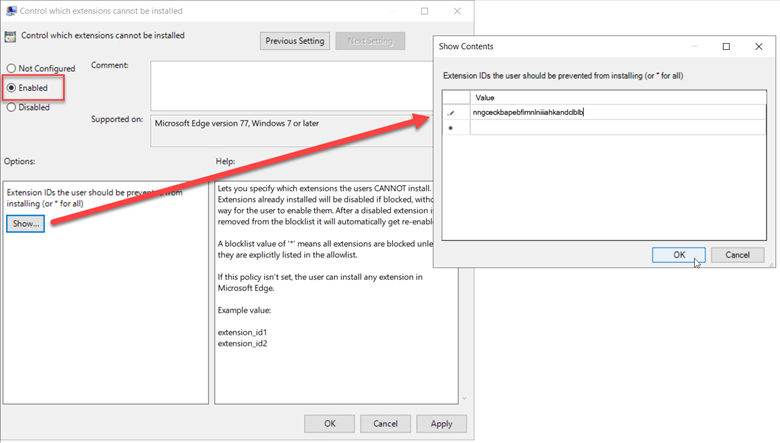
We can do the same thing using Group Policy for the LastPass web extension ID (nngceckbapebfimnlniiiahkandclblb).
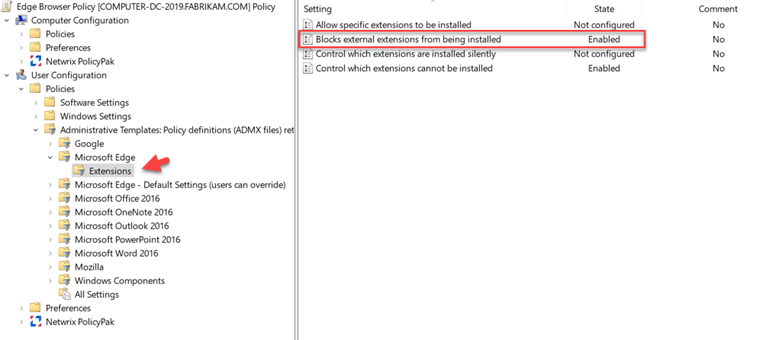
You would then follow this up by enabling the “Blocks external extensions from being installed” setting to prevent all other extensions from installing as shown in the screenshot below.
Configuring the Home Page
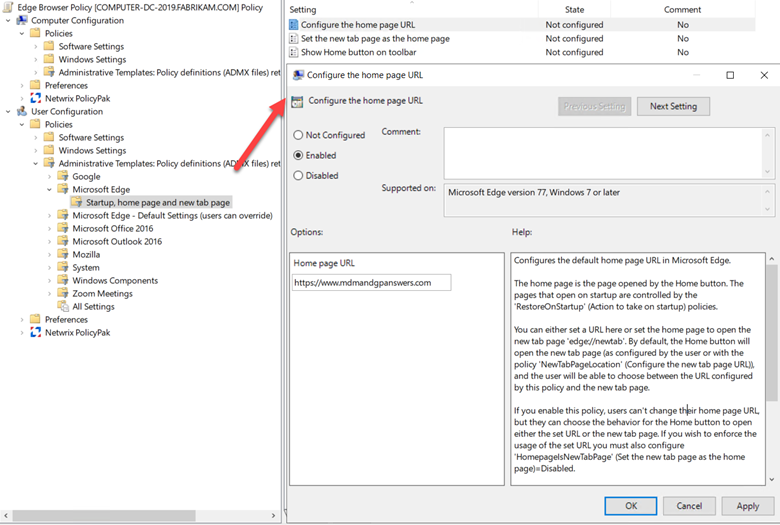
We will wrap up this discussion by assigning a mandatory home page for all users. You can find this setting in Group Policy by going to Administrative Templates > Microsoft Edge > Startup > and enabling the “Configure the home page URL” setting and inputting the desired home page.
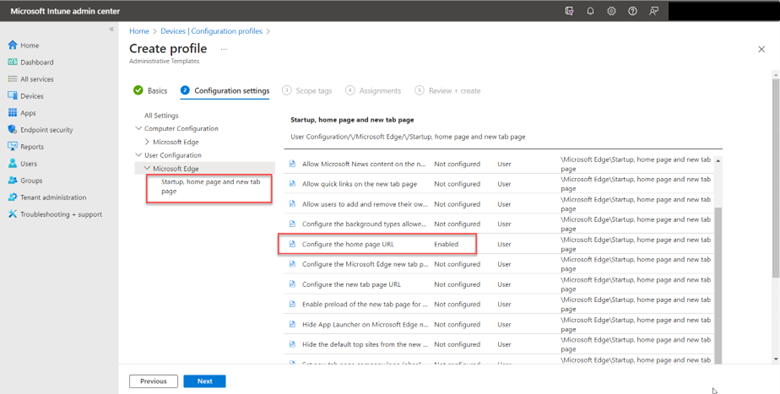
You can do the same with Intune as shown in the screenshot below.
Of course, there are many other settings you can add to your Edge policy. Always test your setting configurations first before implementing them in a production environment.