Creating Security Baselines in Microsoft Intune
Security baselines are used to standardize and enforce security configurations across devices to reduce vulnerabilities and ensure compliance. They allow organizations to rapidly deploy a hardened, secure configuration across their managed Windows devices. The baselines contain groups of pre-configured settings recommended by Microsoft's product security teams, saving significant time and effort in researching and testing individual settings. Pre-configured baselines simplify the deployment of security settings to make it easier for IT administrators to apply comprehensive security policies without having to configure each setting manually. By using predefined baselines, administrators can save time and effort compared to developing and implementing custom security policies from scratch.
Security baselines can be deployed using either Group Policy or Microsoft Intune. Group Policy baselines are typically managed by importing the latest Microsoft Security Compliance Toolkit baselines and customizing settings via GPOs while Intune security baselines are managed directly in the Intune admin console, where admins can create profiles based on the built-in Microsoft-provided baselines and customize settings.
While providing a solid security foundation, baselines can also be customized to meet the specific needs of an organization by adjusting the pre-configured security settings as required. You can assign different Intune security baselines to different user or device groups. This allows you to tailor the security configurations based on specific requirements or roles within your organization. After creating the desired security baseline profiles, you can assign each profile to different user or device groups within your Intune environment. This allows you to apply distinct security configurations to different sets of users or devices based on their roles, locations, or other criteria.
Deploying Security Baselines with Intune
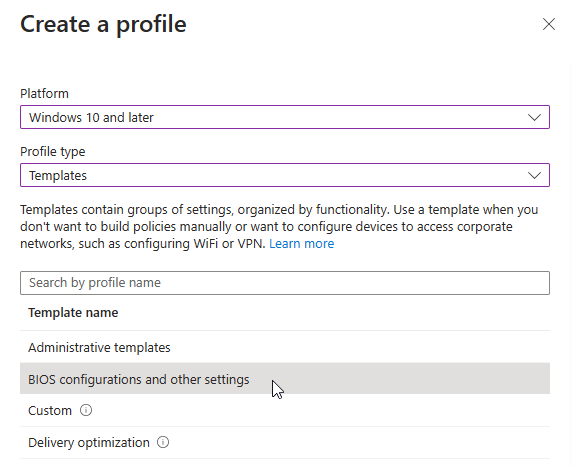
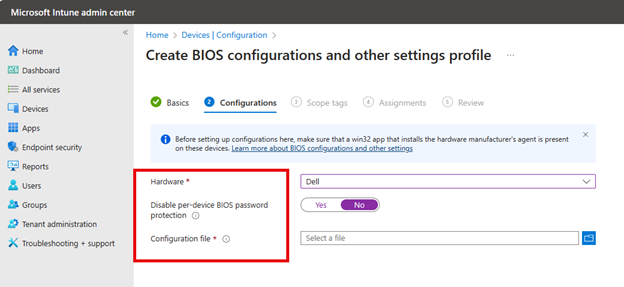
To deploy security baselines using the Microsoft Intune admin center, navigate to Endpoint security > Security baseline and select from the available security baselines. For this example, I will choose the 'Security Baseline for Windows 10 and later' and customize it.
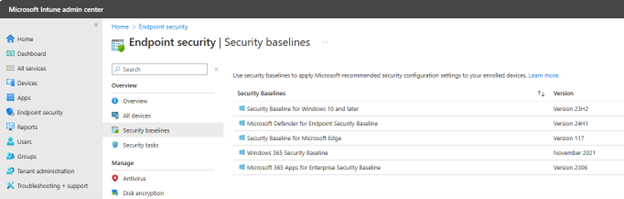
After clicking the selected baseline, click the ‘Create profile’ button to create a new profile.
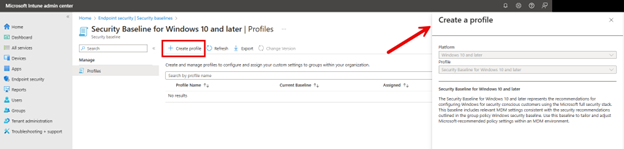
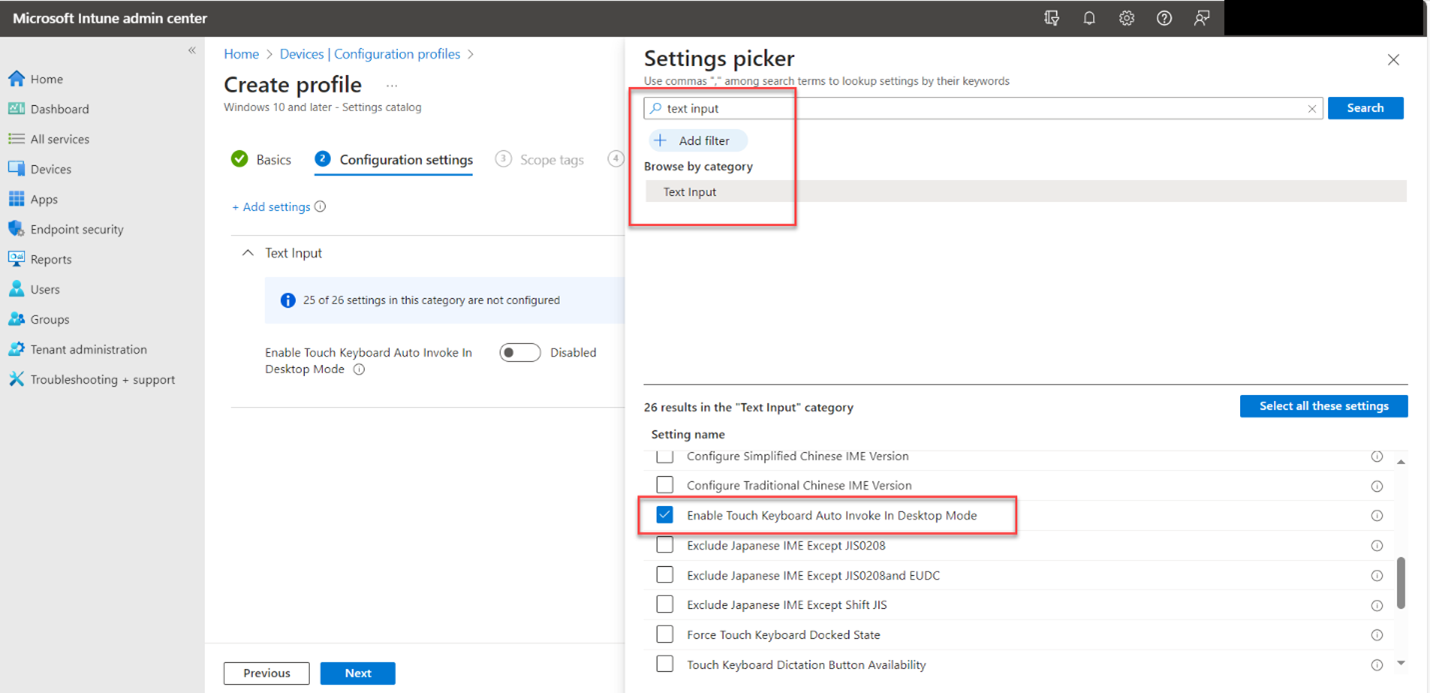
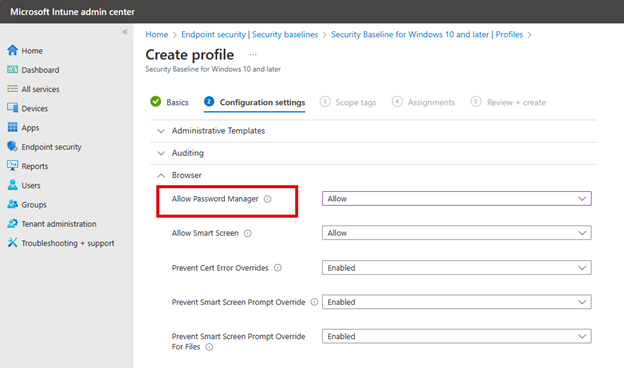
Name the new profile and then proceed to the Configuration settings section. The baseline template has all the settings configured according to best practices by Microsoft engineers. However, there are a couple of settings I want to customize in this case. For instance, the Allow Password Manager setting is configured to Block by default, but in this case, I want to allow it for certain user roles.
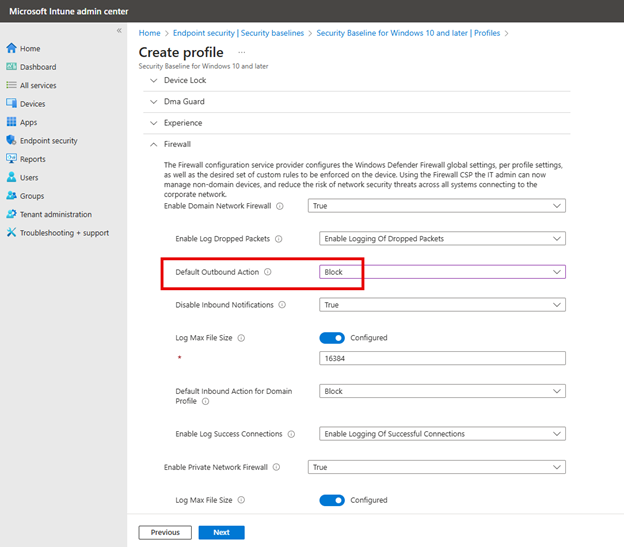
Another setting I chose to change is to block outbound traffic which is not the case by default.
Of course, I could also choose to accept all the preconfigured settings as they are and create a profile too. In this case, deploying the preconfigured baseline makes it convenient to blast out best practice security settings.
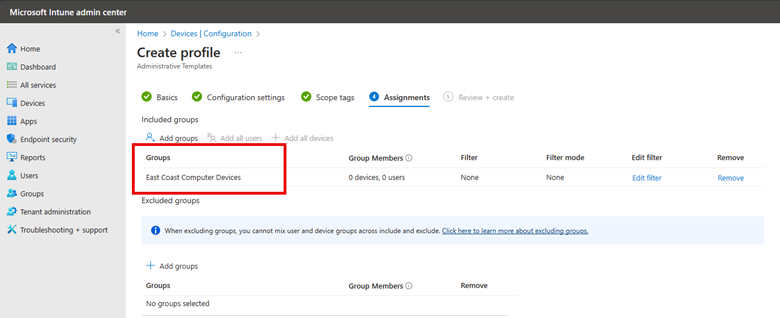
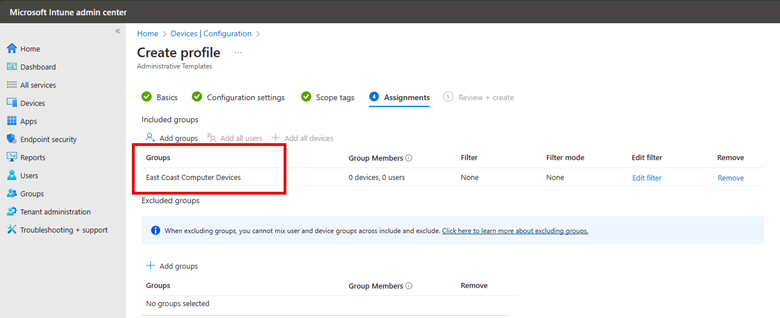
In the same manner that Intune configuration profiles are created, you need to assign this customized security baseline profile to designated groups and then finish out the wizard. You can create as many profiles of the same security baseline as you want. By assigning different Intune security baselines to different user or device groups, you can effectively implement a tailored and granular security strategy that aligns with the specific needs and risk profiles of various segments within your organization.