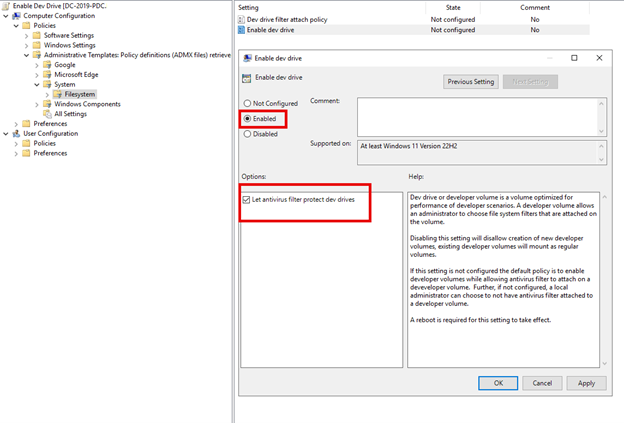
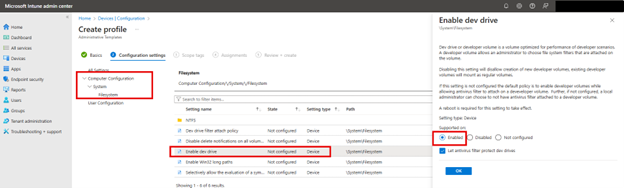
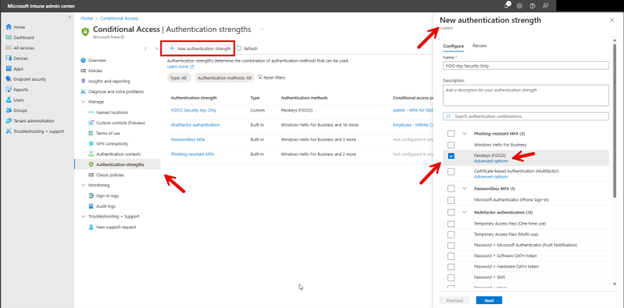
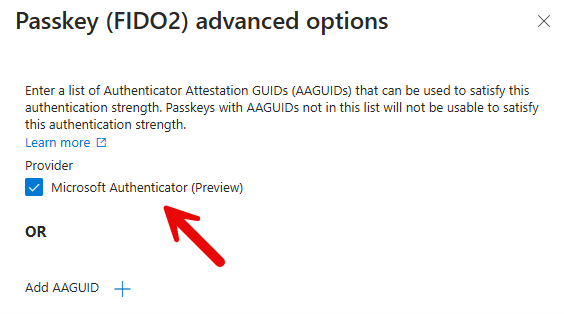
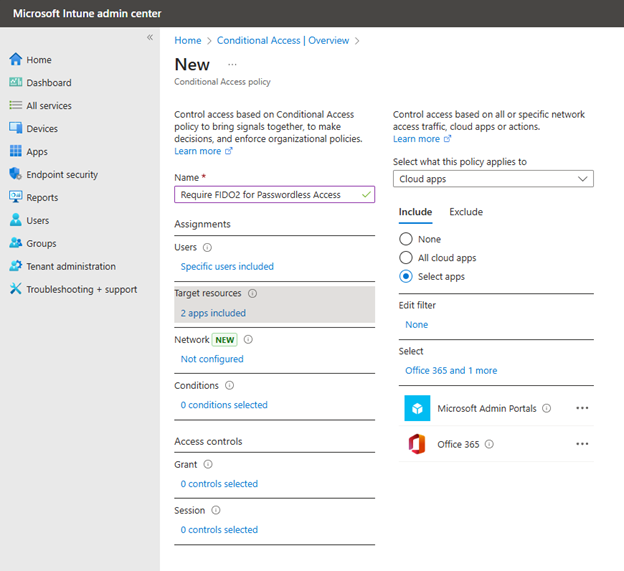
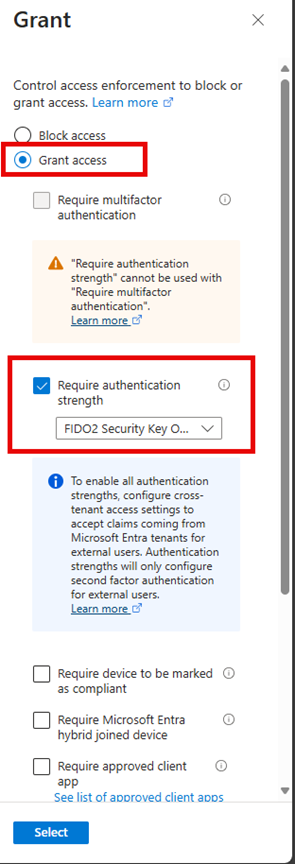
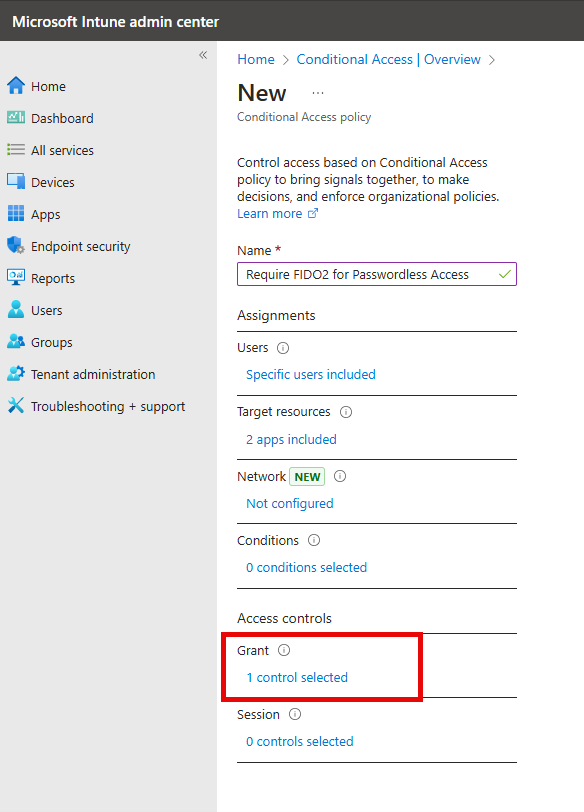
The Microsoft Intune Admin Center enables you to create Conditional Access policies based on locations for additional granular control over access to organizational resources. This feature is particularly valuable for entities with geographically limited operations, such as school districts, government institutions, or regional businesses.
For instance, if your organization's users are primarily located within a single country, you can implement a policy that restricts logins from all other countries. This approach significantly enhances your security posture by mitigating risks associated with global cyber threats.
By leveraging Named Locations in Conditional Access policies, you can effectively:
1. Block access attempts from unexpected geographical areas
2. Reduce the attack surface for brute force and credential stuffing attacks
3. Minimize the risk of unauthorized access from foreign IP addresses
By restricting access from unfamiliar or high-risk locations, organizations can reduce the risk of unauthorized access and potential security breaches.
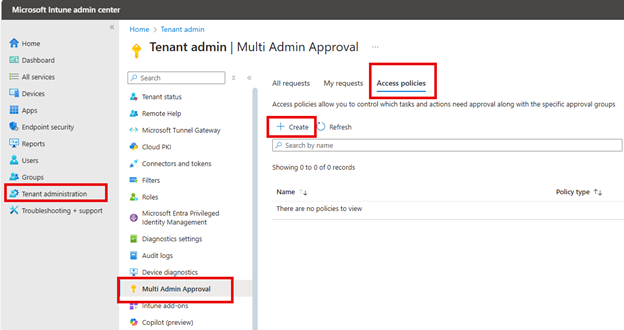
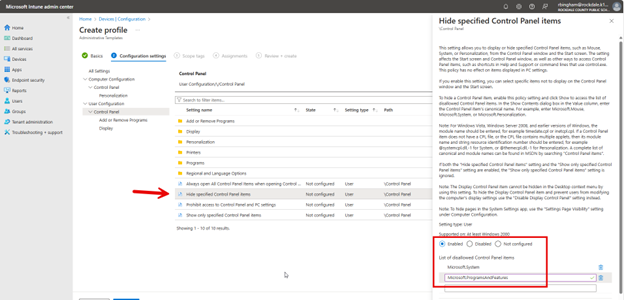
Create Country Locations
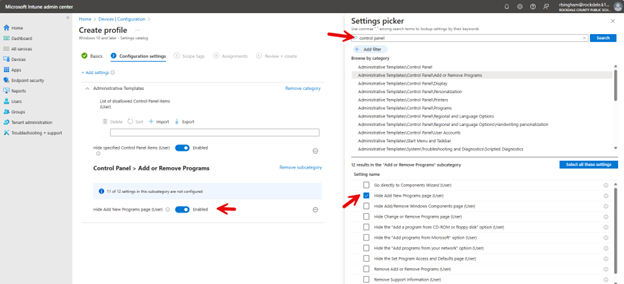
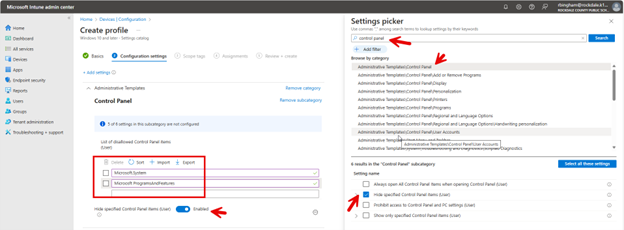
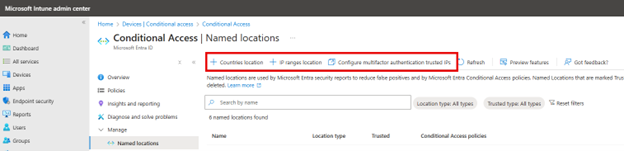
To create these location areas, you need to navigate to Devices > Conditional Access > Named Locations. Here you can create locations according to Countries, IP addresses and Multifactor Authentication Trusted IPs as shown below.
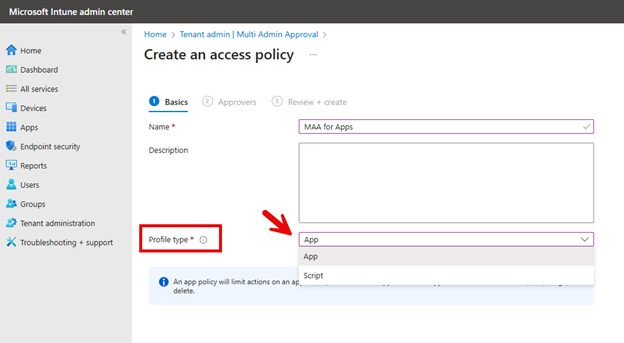
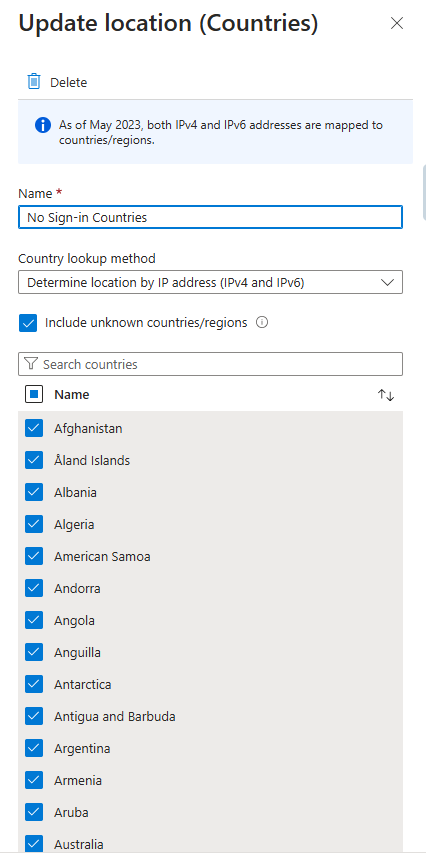
Let’s say you want to create a conditional access policy that stops all login attempts from other countries. Click Countries location and select all countries outside of your own as shown here.
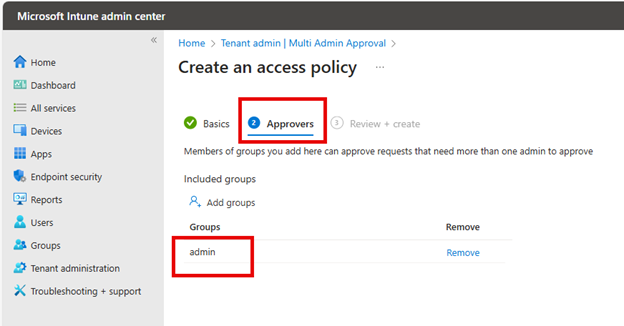
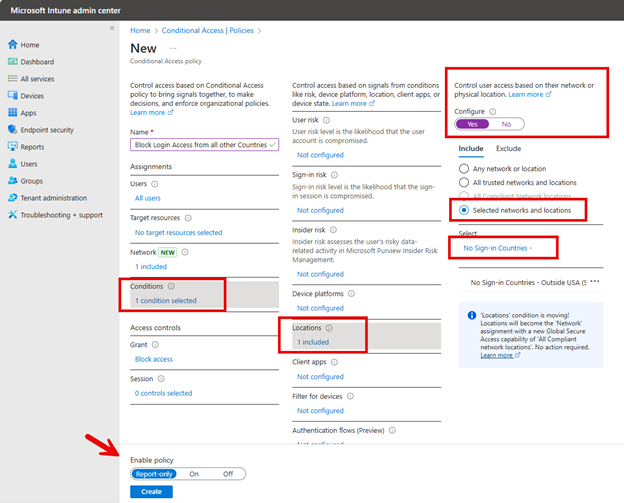
Once you've defined the Named Location, you can proceed to create a corresponding Conditional Access policy. Configure the policy to use the location condition, selecting the Named Location you've previously defined. You may want to initially enable the policy in "Report-only" mode. This allows you to monitor its potential impact without affecting user access. You also need to be mindful of employees who travel internationally as this may require you to:
a) Create exceptions for specific users or groups
b) Implement a process to temporarily modify the policy for traveling employees
c) Create a traveling policy that allows access from all countries and assign it to anyone traveling temporarily.
The screenshot below shows how anyone attempting access from all other countries of the world will be blocked.
Other Location Scenarios
You can also create locations based on IP addresses or ranges. You can use these locations for a variety of instances. For instance, you can create policies that differentiate between office locations and remote work environments that apply security measures differently for set locations. You also may be receiving failed login attempts from a certain IP address and make a conditional access policy to block it.
You can also create trusted IP locations to coincide with your MFA conditional access policies. In this scenario, all logins except those originating from your trusted IP ranges. Users connecting from trusted locations will not be prompted for MFA, while those connecting from outside these ranges will need to complete MFA.