Using Group Policy to Enforce Resiliency
Traditional cybersecurity approaches have primarily focused on attack prevention through measures like firewalls, antivirus software, and access controls. Recently however, cybersecurity has transitioned to a resiliency mindset. With the rise of advanced persistent threats (APTs), state-sponsored attacks, ransomware, and other sophisticated cyber threats, it has become increasingly difficult to prevent all attacks through traditional security measures alone. Resiliency acknowledges that breaches are likely to occur and focuses on minimizing their impact and ensuring continuity of operations.
At any moment, attackers can begin exploiting a vulnerability that is unknown to anyone in the world except themselves. These zero-day attacks are particularly challenging because you cannot defend against a threat you are unaware of. The compromise of user accounts has also become common place using phishing and credential stuffing attacks. It has become clear that organizations must prepare themselves for the inevitability that such attacks are probably going to occur. By fostering resilience in their systems and networks, they can limit the blast zone and prevent attackers from moving laterally across the network and obtaining greater privileges. A resilient approach acknowledges that breaches are likely to happen and focuses on minimizing their impact and ensuring continuity of operations.
How Group Policy can Help
A primary means of building resilience within your enterprise is to enforce the principle of least privilege (PoLP). PoLP minimizes security risks by ensuring users and systems have only the necessary access to perform their tasks. This reduces the potential attack surface, limits the impact of breaches, and prevents unauthorized access to sensitive data, thereby enhancing overall cybersecurity in an increasingly complex and threat-prone digital environment. Here are some classic Group Policy settings to harden your attack surface.
You can quickly restrict access to the command prompt completely with User Configuration > Administrative Templates > System and enable ‘Prevent access to the command prompt’. For additional security, you can select ‘Disable the command prompt script processing also’ as shown in the screenshot below. This means that any script that attempts to execute a batch file will fail, and users will not be able to run batch scripts manually.
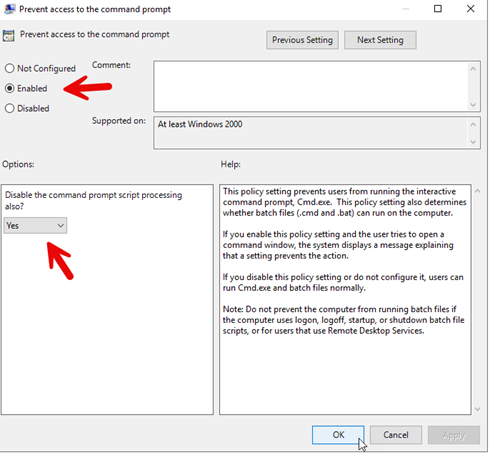
By disabling both the command prompt and script processing, this setting significantly enhances security by reducing the potential for users to execute potentially harmful scripts or commands.
Enforcing the membership of privileged local groups on all your enterprise computers is a crucial aspect of resiliency building. You can achieve this using either Group Policy Preferences or the Security Settings in Group Policy. In the example below, I have chosen the latter approach. I navigated to **Computer Configuration** > **Policies** > **Windows Settings** > **Security Settings** > **Restricted Groups**. I then selected the local Administrators group and specified domain admins as the only members, as shown below.
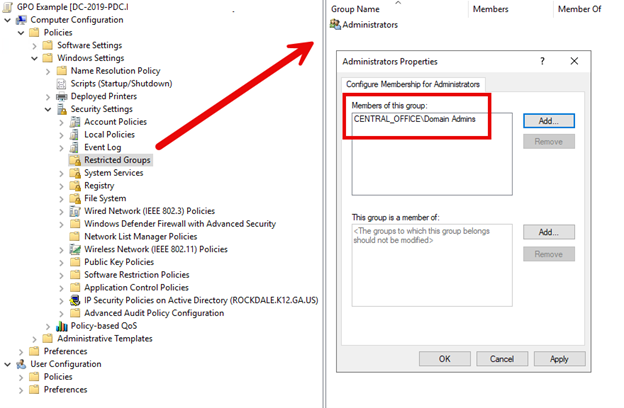
These examples illustrate how you can leverage Group Policy to enhance the resilience of your Windows machines against various threats and vulnerabilities. By implementing settings through Group Policy Administrative Templates and Preferences, you can enforce robust security configurations across your Windows environment.
However, these are just a few of the many resilience-focused measures that can be deployed using Group Policy. In the next installment of this article series, we will explore additional resilient settings and configurations that can be implemented through Group Policy to further fortify your Windows infrastructure against cyber threats, insider risks, and potential misconfigurations.




Comments (0)