Use Device Tags to Simplify Intune Management
Admins can tag devices using Microsoft Intune to enhance device management, organization, and security across their enterprise environment. Tags can be used to efficiently group and categorize devices based on various attributes such as department, location or function. This logical grouping enables IT teams to apply policies, updates and security measures more effectively. Tags can be automatically assigned and updated through dynamic rules, ensuring that device classification remains accurate and up-to-date. Some of the applications of tagging includes the following:
- Tags can be used to filter and search for specific devices in large environments to improve management efficiency.
- Tags can be used to apply specific policies, configurations, or software to groups of devices that share common characteristics.
- Tags can help in tracking and managing hardware assets across an organization.
- Tags can be used to identify devices that require specific security measures or compliance checks.
- Tags can provide additional context about devices, which can be helpful during troubleshooting or decision-making processes.
In other words, tagging provides numerous management options and can prove a way to simplify your MDM efforts.
Create a Configuration Policy
To implement tagging using the Microsoft Intune Admin Center, navigate to Devices > Configuration > Policies > and create a new policy. Choose Windows 10 and later as the Platform and select Custom Templates as the Profile type.
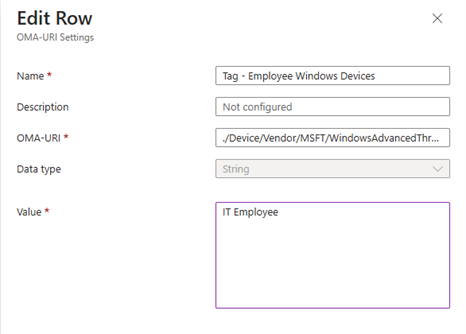
You will then apply a name for the policy and configure the OMA-URI Settings. The OMA-URI path is the most critical here so use the following path:
./Device/Vendor/MSFT/WindowsAdvancedThreatProtection/DeviceTagging/Group
In the example below I selected String as the data type and made a tag called IT Employee.
You could also use a PowerShell script to create tags and deploy the script through Intune. I can then create a dynamic group in Azure AD that includes all devices with the “IT Laptop” tag. Security policies and configuration policies could then be applied to devices belonging to the IT role group.




Comments (0)