The Many Ways to Block Access to Windows Command Prompt using Intune or Group Policy
Since the early days of Group Policy, I have been talking about the importance of blocking Windows command prompt for non-administrative users. While it is an essential tool for IT personnel, in the wrong hands, the command prompt can be used to execute potentially harmful commands, access sensitive system files, modify system settings, run malicious scripts, or launch programs that could compromise system integrity. Even barring malicious intent, preventing access helps maintain system stability by preventing accidental misuse of powerful command-line tools that could disrupt operations or expose confidential data.
While the objective may be the same, there are multiple methods to implement this policy in modern IT environments. Let’s explore the various ways to achieve this security measure using Group Policy, Microsoft Intune and the Intune Education portal.
Using Group Policy
The way to block access to Windows Command Prompt using Group Policy hasn’t changed at all over the years. It is still a straightforward approach. Simply create a new GPO and navigate to User Configuration > Administrative Templates > System > and enable the policy setting “Prevent access to the command prompt" as shown in the screenshot below:
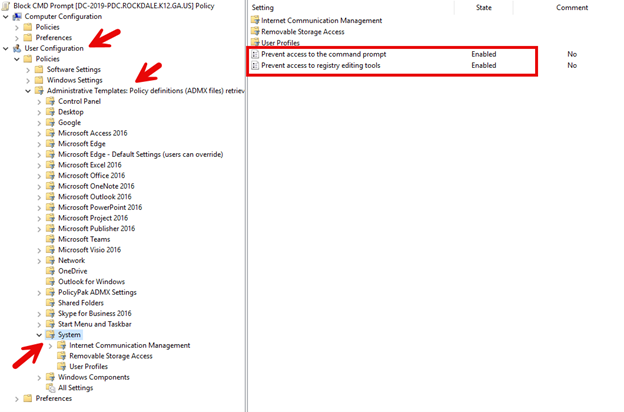
Note that the setting, “Prevent access to registry editing tools” has been enabled which as well and is highly recommended.
Using Intune Settings
Settings Picker
When we start talking about Microsoft Intune, there are multiple ways to block access. The simplest approach is to use the Settings Catalog Configuration Profile. Using the Microsoft Intune admin center, navigate to Devices > Configuration > Create > New policy. Choose Windows 10 and later as the Platform and Settings catalog as the Profile type. Do a search for “CMD” and browse Administrative Templates\System. Then enable the “Prevent access to the command prompt (User)" setting” and choose the “Disable the command prompt script processing also? (User)" if desired. These steps are outlined in the screenshot below.
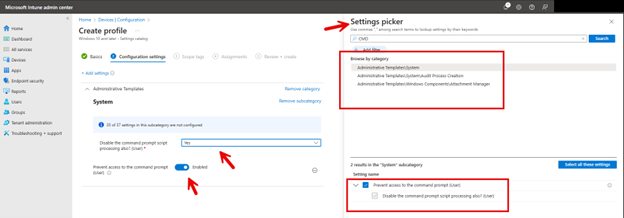
Note that until December 2024 you could use Administrative Templates to create a new configuration profile to block CMD access. Microsoft has now phased out the use of Administrative Templates for creating new configuration profiles to block CMD access.
OMA-URI Settings
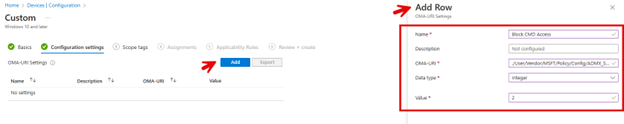
You can also create a Configuration profile using OMA-URI settings. Here are the settings:
- OMA-URI path: ./User/Vendor/MSFT/Policy/Config/ADMX_ShellCommandPromptRegEditTools/DisableCMD
- Data type: Integer
- Value: 1 (to block) or 2 (to block and disable scripting)
See the screenshot below for an example:
AppLocker Settings
If you've already created an AppLocker Group Policy that successfully blocks the CMD prompt, you can leverage this existing configuration in Intune. Extract the XML content from your Group Policy and deploy it through Intune using OMA-URI settings.
- OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/EXE/Policy
- Data type: String
- Value: (Paste the XML content of your AppLocker policy here)
Education Portal Method
Some educational institutions with limited IT resources opt for the Education version of Microsoft Intune. This simplified platform is designed to be more accessible, allowing staff members with basic technical knowledge, such as teachers with some IT background, to manage and implement fundamental Mobile Device Management (MDM) policies.
You can access the Intune Education portal at (https://intuneeducation.portal.azure.com/). Then navigate to Groups > All Devices > Settings > Windows Device Settings > Apps. Use the "Block Access to Administrative Apps" option as shown in the screenshot below.
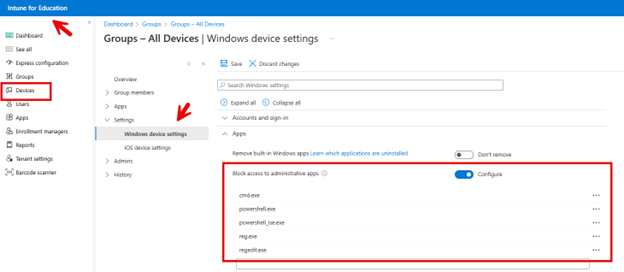
Note that by default, this setting also blocks access to other system apps such as PowerShell and regedit.




Comments (0)