Lock Down the Windows Settings App with Intune
In the past, group policy administrators focused on limiting standard users' access to various sections of the Windows Control Panel. Today, while controlling access to the Control Panel remains important, it's equally crucial to restrict access to the Windows Settings app. This approach is driven by several key objectives:
- Prevent unauthorized modifications that could undermine system security.
- Ensure compliance of regulatory standards
- Enhance the reliability of client devices and systems to reduce ticket volume.
- Safeguard against both accidental and deliberate data loss scenarios.
- Ensure computers are optimized for business-critical functions.
- Facilitate device management and troubleshooting by maintaining consistent settings across the organization.
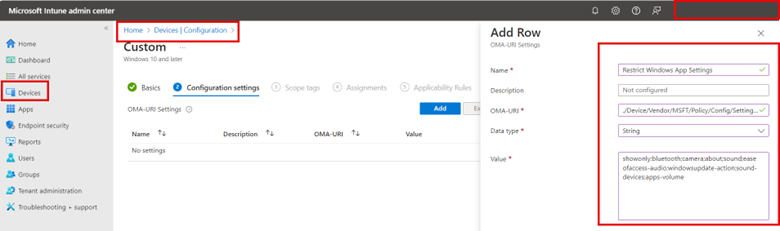
One way to approach this is rather than creating an Intune policy that restricts access to specific ms-settings, you use an allow list approach that only allows access to a specific list of settings. To do so using the Microsoft Intune Admin Center go to Devices > Configuration and click “Create” to make a new profile. Choose Windows 10 and later as the Platform and Custom Templates as the Profile type.
Using custom templates, assign the profile a name and apply the following OMA-URI settings:
OMA-URI: `./Device/Vendor/MSFT/Policy/Config/Settings/PageVisibilityList`
Data type: String
For the String value, type showonly: and list each msi-setting you want immediately after the colon. Separate each msi-setting with a semicolon like this:
showonly:bluetooth;camera;about;sound;easeofaccess-audio;windowsupdate-action;workplace-provisioning;sound-devices;apps-volume;privacy-webcam
The screenshot below shows the process using Intune:
Complete the profile by adding any desired scope tags and assign the profile to your designated groups and finish the wizard.
You can find a complete list of ms-settings names on the Microsoft website.




Comments (0)