How to Use Security Baseline Releases for Windows 11-2
Microsoft has a new operating system, which means we need a new security baseline. Microsoft released the new package on October 5 which features two new settings and some recommended setting changes. The Security Baselines for Group Policy are designed around the same principle as the MEM Security Baselines. They provide an easy and effective way for admins to ensure that they are consistently enforcing a minimum-security level that addresses fundamental security and compliance issues. The baseline settings are preconfigured by Microsoft security specialists and have been tested for proven compatibility.
Installing the Windows 11 Security Baselines
Once you download the package you will see that it contains multiple folder directories as is shown below.
If you don’t have the Windows 11 ADMX/ADML templates, you can copy them from the Template folder and paste them into your central store. The templates are shown below.
The real purpose of the package is to import the new security baselines. You can import these policies either locally or into AD using the enclosed scripts. I am choosing to import them into my AD environment using the appropriate scripts as shown below.
Domain Security GPO
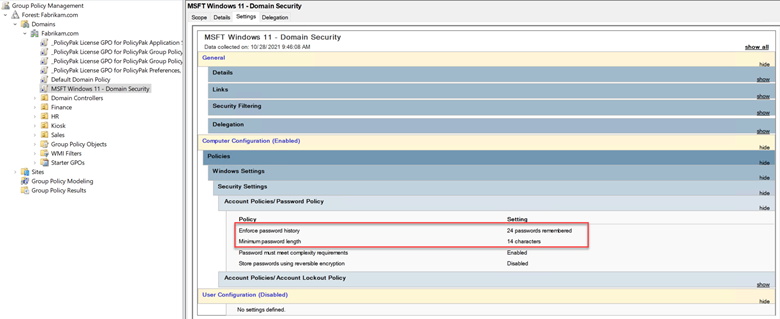
Let’s look at some of the settings included in the package. The package includes a GPO called MSFT Windows 11 – Domain Security. A big change here is the recommended password length. While a 14-character password has been supported on multiple Windows 10 versions, Security Baselines have continued to enforce an 8-character password length only, which remains a standard in the industry. The Windows 11 baseline has now increased the minimum password length to 14-characters as shown in the screenshot below. Advanced password breaking applications powered by readily available increased CPU power has made the 8-character passwords far too vulnerable as they can be potentially cracked in mere hours.
It is highly recommended that you confirm that all your systems and applications are compatible with a password of this length before you enact this policy. It’s a good idea to first Enable the ‘MinimumPasswordLengthAudit’ Group Policy setting which is located at Computer Configuration > Windows Settings > Security Settings > Account Policies -> Password Policy -> Minimum password length audit. Enabling this setting will provide insights into the potential impact of increasing your password length.
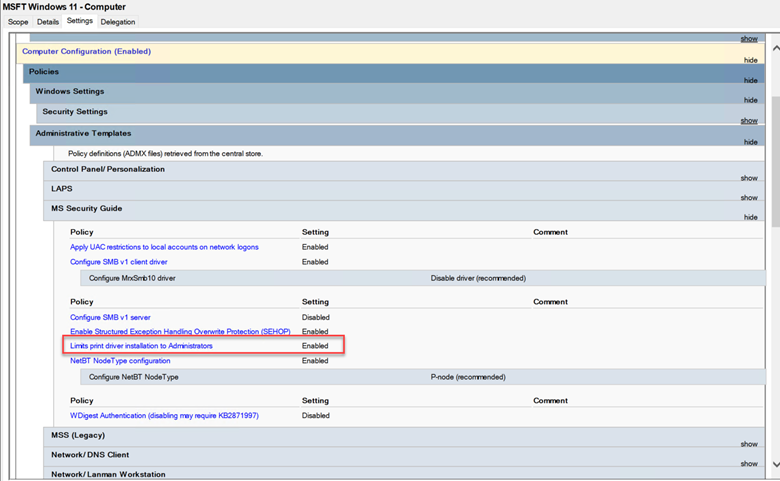
Restrict Printer Driver Installations
In July of 2021, Microsoft released CVE-2021-34527 which patched a remote code execution vulnerability in the Windows Print Spooler service. Essentially, it prevents non-admin users from installing a print driver, which caused a great deal of havoc early on as enterprises that freely allowed standard users to install print drivers were inundated with calls to the helpdesk. I wrote a blog back in August called the Utlimate Guide to PrintNightmare that lists the options you now have as a result of the update. Note that Microsoft has added this setting to the Windows 11 Security Baseline as is shown in the screenshot below.
Microsoft Legacy Edge is No More
As Microsoft Edge Legacy reached EOL earlier this year, it is not a part of Windows 11. That means that all its supported settings have been removed from the baseline. Only Chromium Edge is now supported.
Script Scanning
According to Microsoft, script scanning was a parity gap between Group Policy and MDM. As the gap has now been closed, Microsoft is enforcing the enablement of script scanning in this baseline. Enabling script scanning means that scripts are scanned before being executed to determine their threat status.
One thing lacking in the Group Policy version of Windows 11 Baseline Security is the ability to enable Microsoft Defender for Endpoint's tamper protection feature which is available using Microsoft Endpoint Manager. Microsoft does encourage you to enable it however using other means. More information here.




Comments (0)