How to Setup Multi Admin Approval with Intune
One of the first objectives of a hacker upon infiltrating a network is to gain access to a privileged identity within your organization. One of the more powerful privileged accounts in your network is probably an Intune admin as these accounts weld a lot of power. Should one of those accounts get compromised, they can do significant list of things to your MDM environment such as deploy a malicious application to your corporate devices such as ransomware or backdoor apps. They could also deploy a harmful PowerShell script or other executable script.
MAA is like MFA
With the rapidly expanding threat landscape of today, relying on a single password to secure user accounts is no longer viable. This is why multifactor authentication (MFA) is now considered best practice, as it provides an additional security layer to protect digital identities. Now let’s apply that same logic to your Intune environment.
You cannot risk the compromise of a single Intune admin account that can then execute malicious tasks at will. Like MFA, Multi Admin Approval (MAA) adds an extra layer of security by requiring multiple administrators to approve certain critical actions before they can be executed. This means that if you create a new policy to deploy an application, that policy will not be enabled until a member of the assigned approval group authorizes the action.
When a Tenant account attempts to modify a resource protected by an access policy, Intune implements withholds applying the change until a member of the designated approval group reviews and authorizes it. This process ensures that critical changes undergo additional scrutiny before implementation. The approver has the authority to either approve the change and allow it to proceed or reject it which will block it entirely.
How to Configure MAA in Intune
Note there are some prerequisites that must be met prior to enabling MAA:
- Multi admin approval requires a minimum of two administrator accounts within your tenant
- Creating an access policy requires that your account be assigned either the Intune Service Administrator role or Azure Global Administrator role.
- To qualify as an approver, an account must belong to the group assigned to the access policy for a specific type of resource.
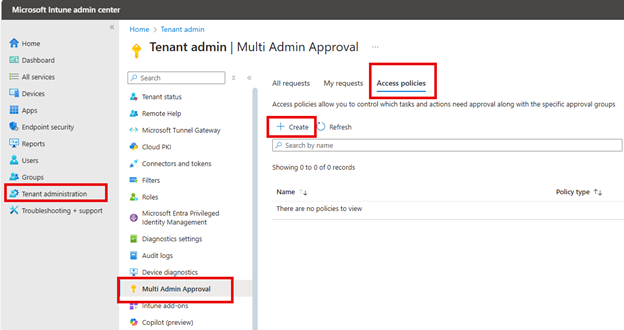
To enable MAA for Intune go to the Microsoft Endpoint Manager admin center and navigate to Tenant Administration > Multi Admin Approval > select Access policies and click Create as shown in the screenshot below.
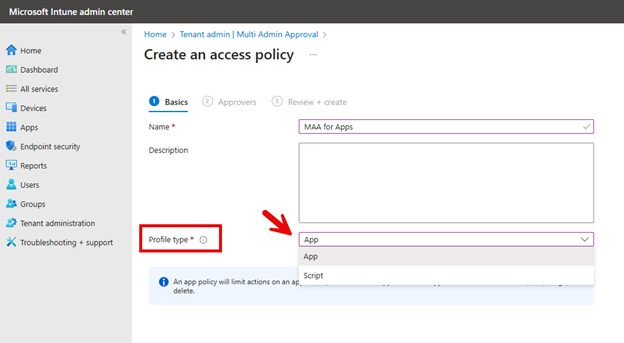
Create a name for the MAA policy and select either Scripts or Apps for the Profile type as shown below.
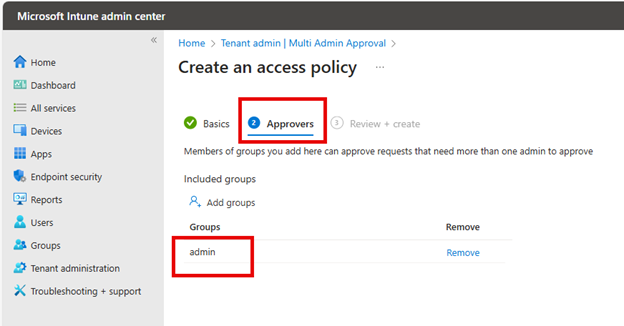
Next is the Approvers page where you will click “Add groups” and select the group of users that will act as approvers for this policy.
Then review and click Create to finalize and save the policy.
Approving Requests
So now let’s say you create an Intune policy to deploy a new application. A new step will be required for you to include the business justification for your request. Rather than an active policy, it is submitted as a request and awaits approval. You can monitor the status of your requests on the MAA page. There you will see a list of all your submitted requests, along with their current status.
The status of your requests can be one of the following:
- Pending: The request is waiting for approval from another administrator.
- Approved: The request has been approved and the changes have been applied.
- Rejected: The request was rejected by an approver.
- Canceled: The request was canceled by you or another administrator.
To approve the request of another admin, simply navigate to Pending requests and select the specific request you want to approve. Make sure that all administrators involved in the approval process are notified of pending actions.




Comments (0)