How to Configure App-Specific Intune Access Controls
If you use Azure AD to host your user accounts, you may want to create conditional access policies for when employees attempt to access certain cloud applications. An example might be an enterprise resource planning solution, an employee benefits site or a password manager. A couple of conditions you can assign might be:
- Require MFA as an extra layer of authentication beyond passwords to reduce the risk of unauthorized access even if credentials are compromised.
- Require that access be only granted from Azure joined devices.
Conditional access policies allow you to safeguard sensitive information and apply stricter controls only where they're most needed. They may also aid in complying with various regulatory requirements and helps mitigate risks associated with remote work.
In this example I am going to create a conditional access policy for LastPass, a password management tool. To create a conditional access policy for a specific cloud application, sign into the Microsoft Intune Admin Center and navigate to Devices > Conditional Access. Click "New policy" to start configuring the new conditional access policy.
Give the policy a descriptive name and go to assignments. For users I chose a group comprised of all IT workers that regularly access many applications. I then selected the two LastPass cloud applications that our organization uses as shown in the screenshot below:
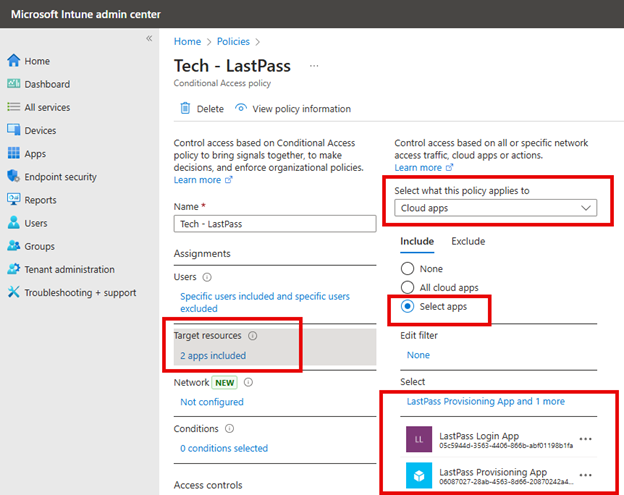
Then under Access Controls I will create two conditions for granted access. The first is MFA and the second is that the user must be using a compliant device as shown below.
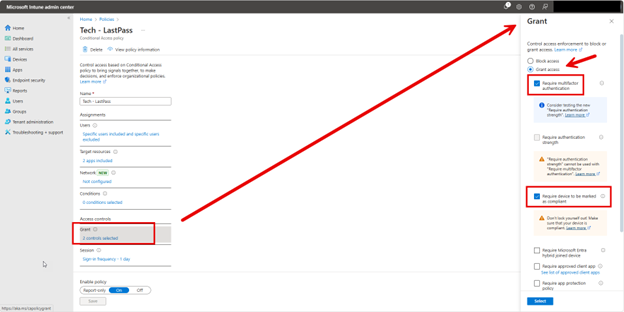
For added security you can specify a sign in frequency under the Session category. Assigning a sign-in frequency requires users to re-authenticate periodically when accessing cloud applications or resources. As shown in the screenshot below, administrators can customize the frequency based on the sensitivity of the applications or data. In this case I am requiring users to reauthenticate each day.




Comments (0)