Create your own Authentication Strengths for Intune MFA
Given the increasing ease with which passwords can be compromised, relying solely on password authentication is no longer a secure method for controlling access. In response to this vulnerability, many companies are now widely implementing Multi-Factor Authentication (MFA) to strengthen their cybersecurity defenses. MFA adds an essential layer of security by requiring multiple forms of verification, such as passwords, security tokens, or biometric scans. This added layer of protection makes it significantly harder for unauthorized individuals to access sensitive data.
Intune provides multiple secure authentication alternatives. Some built in options include Passwordless MFA that includes phishing resistant methods that use Microsoft Authenticator. It also includes the use of FIDO2 security keys and Windows Hello for Business. Intune. In the case of FIDO2 keys, you can restrict authentication to specific manufacturers.
Custom Authentication Strengths
Microsoft Intune provides administrators with the flexibility to create tailored authentication requirements that can precisely match their organization's security needs. Administrators can create up to 15 custom authentication strength using the following authentication methods:
- Password
- SMS
- Voice call
- Microsoft Authenticator app (push notification)
- OATH hardware token
- OATH software token
- Windows Hello for Business
- FIDO2 security key
- Certificate-based authentication
You can use different combinations to enforce specific authentication methods for different scenarios. For instance, different authentication strengths can be required based on whether users are accessing resources from inside or outside the corporate network. Stronger authentication methods can also be required for users or sign-ins deemed high-risk.
To create new authentication strengths using Microsoft Intune Admin Center and navigate to Conditional Access > Authentication strengths and click "New authentication strength". Then select the desired authentication method. In the example below I made a authentication strength for Passkeys FIDO2.
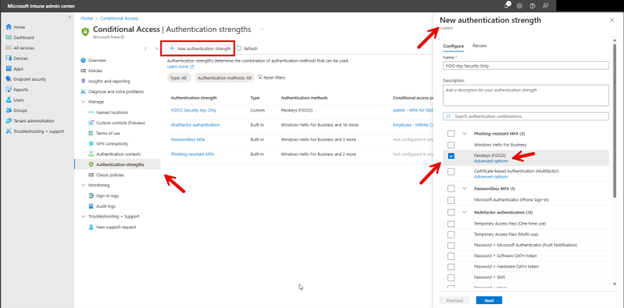
I then clicked the advanced options and chose checked Microsoft Authenticator (Preview).
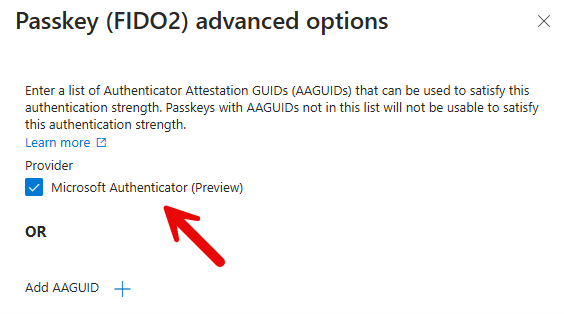
Then click create and you are one.
Creating a Conditional Access Policy
Now let’s use the new authentication strength in a conditional access policy. Return back to Conditional Access and click “Create New Policy.” Then do the following:
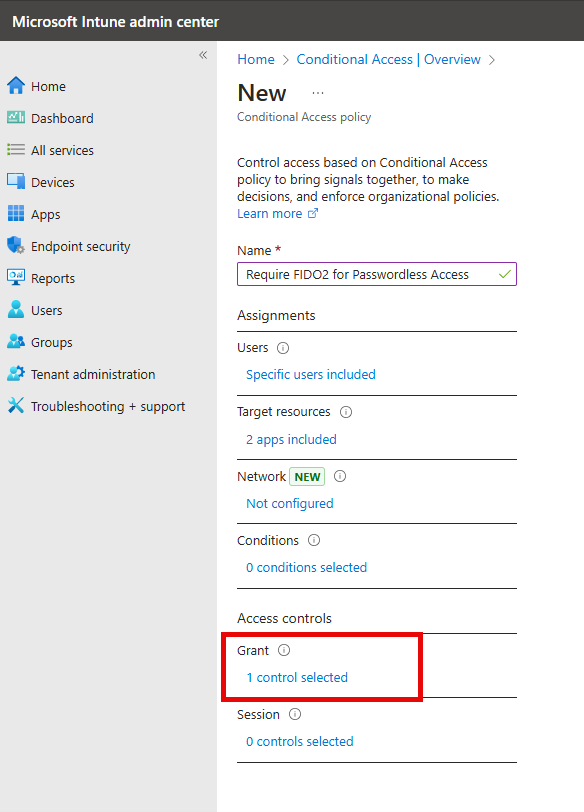
- Give the policy a descriptive name such as "Require FIDO2 for Passwordless Access".
- Under "Users and groups", select the users or groups you want this policy to apply to.
- Under "Cloud apps or actions", select the applications you want to protect as shown in the screenshot below
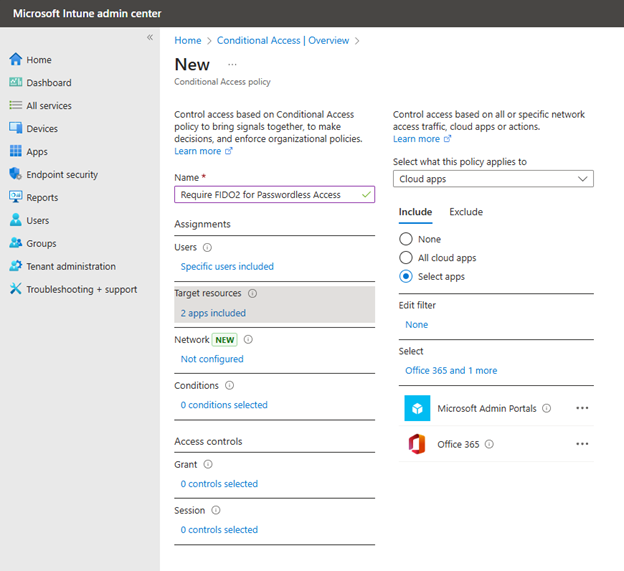
You can then choose the conditions that will trigger the policy such as User risk level, device platform or location.
To configure the Access controls, go to Grant and select Require authentication strength" and select an existing custom strength. You can also create a new authentication strength here as well.
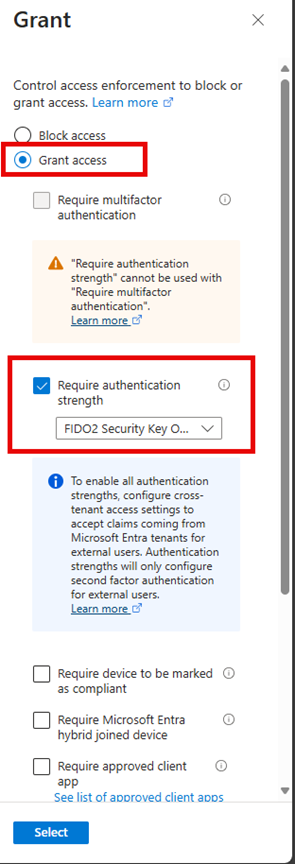
The Grant section will now show 1 control selected as shown below.
Now Set "Enable policy" to "On" and create the policy. You have now created a conditional access policy with your custom authentication strength.




Comments (0)