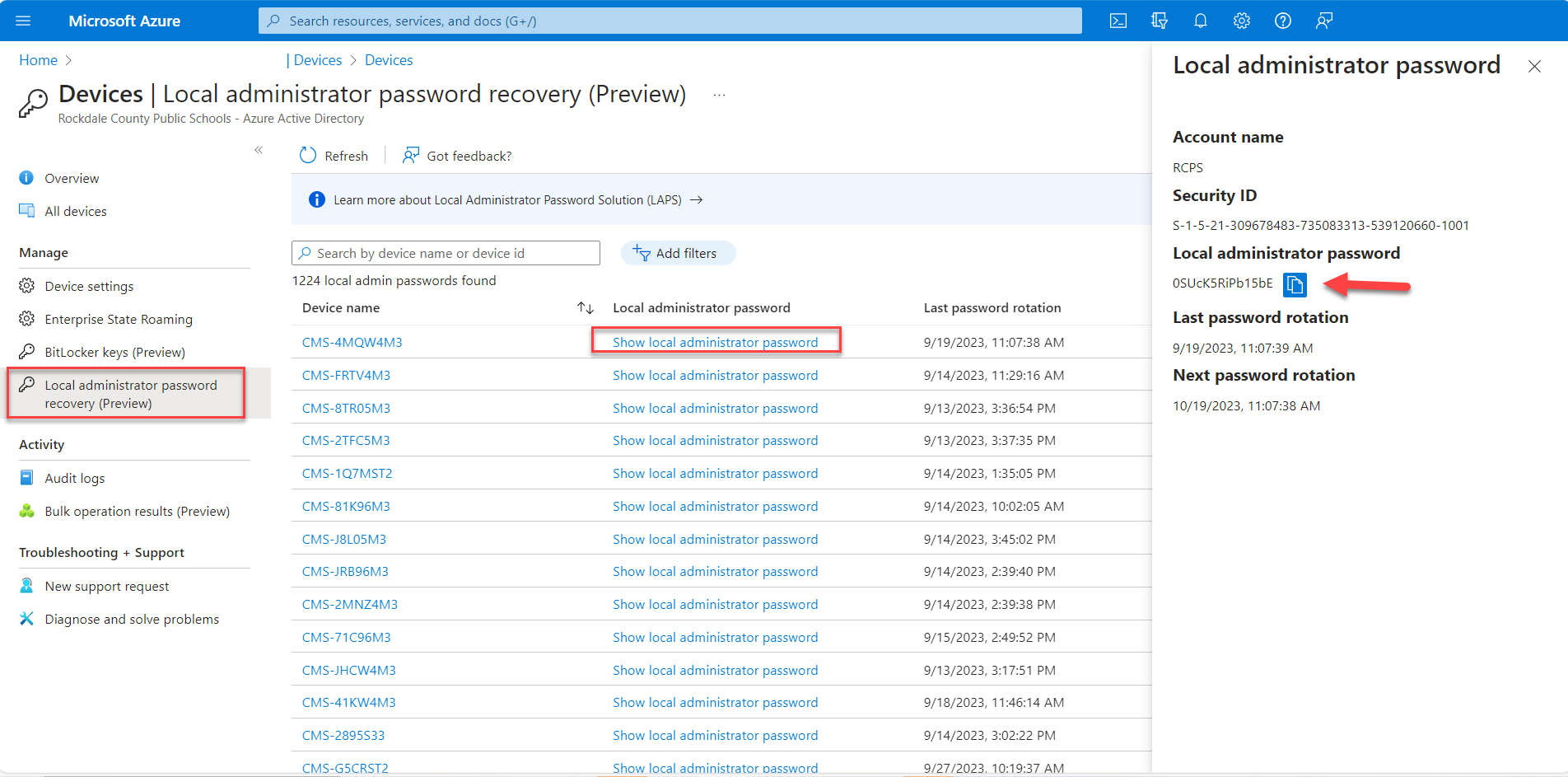
In an earlier blog I talked about Windows LAPS (LAPS2) that was released in April 2023. It was designed to replace the original version of LAPS, now known as Legacy LAPS. We explored its integration in an on-prem AD setting across multiple articles. Today, let's pivot to applying it within the Azure AD framework.
Windows LAPS is designed to help bolster security by minimizing the risk associated with compromised local administrator passwords that could grant unwarranted access to networked Windows devices. A prevalent scenario in many enterprises is the use of a uniform local admin account across all Windows endpoints, characterized by an identical username and password. This poses a significant security gap because if a single account is breached, a threat actor could potentially gain administrative access to every interconnected device. In the case of a school district, once one student gets a hold of the local admin credentials, it doesn’t take long until the entire student body has admin rights, wreaking havoc on the machines.
Windows LAPS ensures each local admin account is assigned a unique password. For instance, if you oversee multiple Windows devices all having a local admin account labeled 'Admin1', Windows LAPS allows you to set a unique password for each of these accounts. Additionally, these passwords come with a specified expiration period, after which a new randomized password is created. While my earlier blog series delved into setting up LAPS via Group Policy, in this piece, we'll explore its configuration using Intune.
PRE-REQUISITES FOR WINDOWS LAPS AZURE AD
The prerequisites for Windows LAPS are few. There is nothing to install because Intune policies are used to configure the LAPS CSP already on the devices. Here is what you need:
- An Intune license
- All computers need to be on Windows 10 or Windows 11 with the April 2023 Cumulative Update installed
- Requires one of the following roles in Azure AD: Global Administrator, Cloud Device Administrator, or Intune Administrator.
Because Azure is cloud based, you can access Windows LAPS from anywhere and Intune’s scalability allows you to easily manage a great many systems. It is important to remember one downside and that is the dependency on the internet. If your internet service is down and you don’t have an alternative means to reach Azure, you will have no way to retrieve the LAPS password. That being said, let’s get to configuring Windows LAPS for Azure AD.
Configuring LAPS for Azure AD
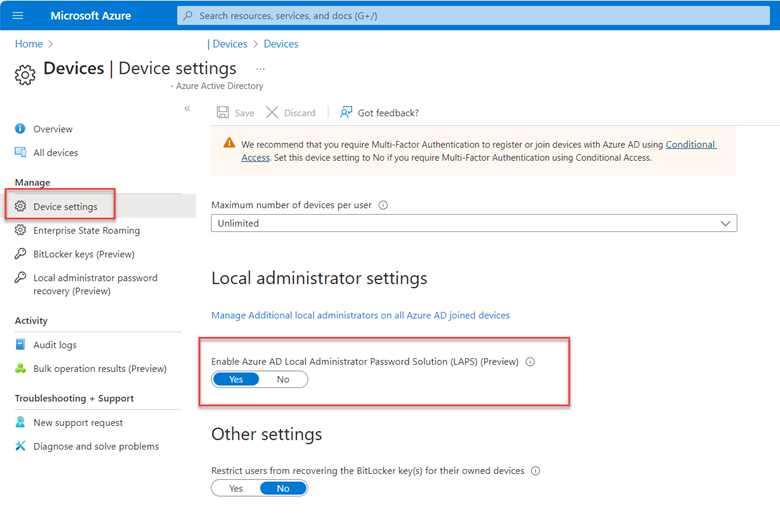
Before you create an Intune policy you must first access your Azure portal (portal.azure.com) and enable LAPS. Navigate to Devices > Device Settings and scroll down. Then turn on the “Enable Azure AD Local Administrator Password Solution” as shown below.
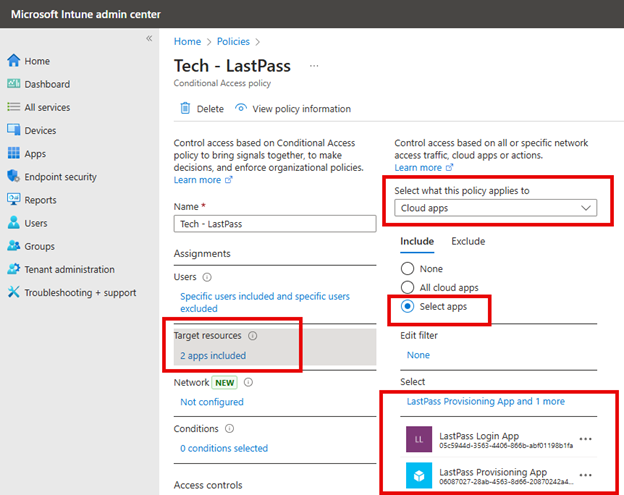
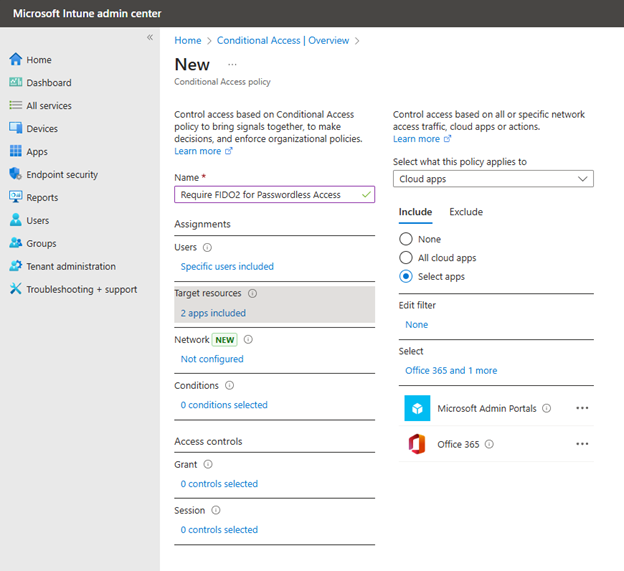
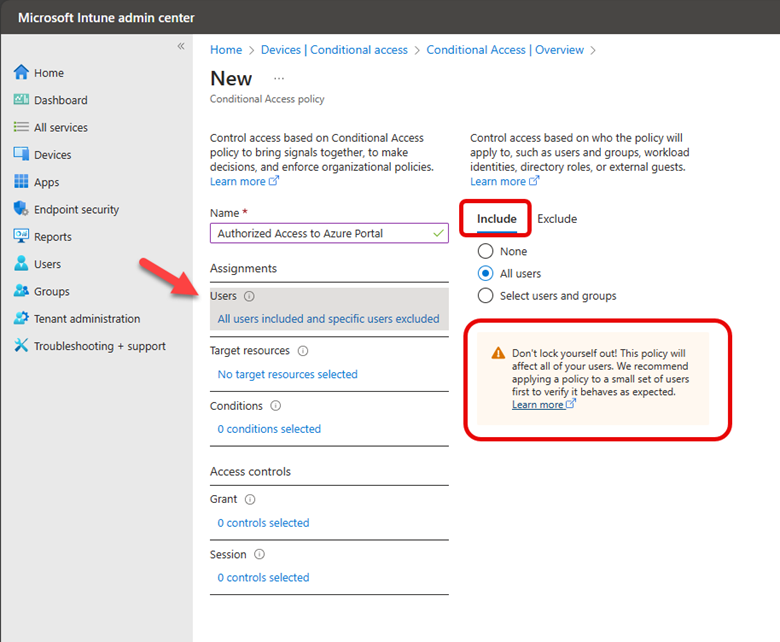
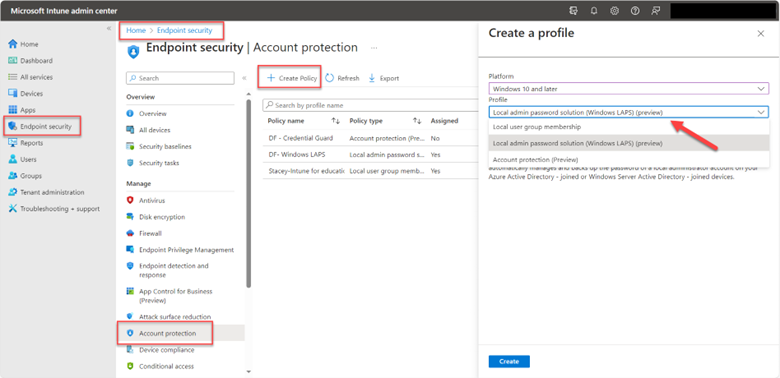
Once that is completed, you can move on to Intune. Using the Microsoft Intune admin center navigate to Endpoint Security > Account protection and click Create Policy. Choose “Windows 10 and later” as the Platform and “Local admin password solution Windows LAPS” as shown in the screenshot below.
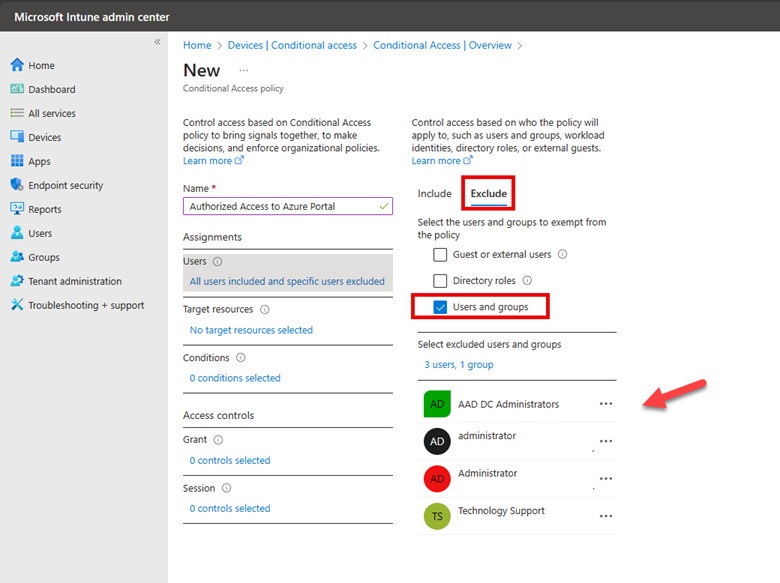
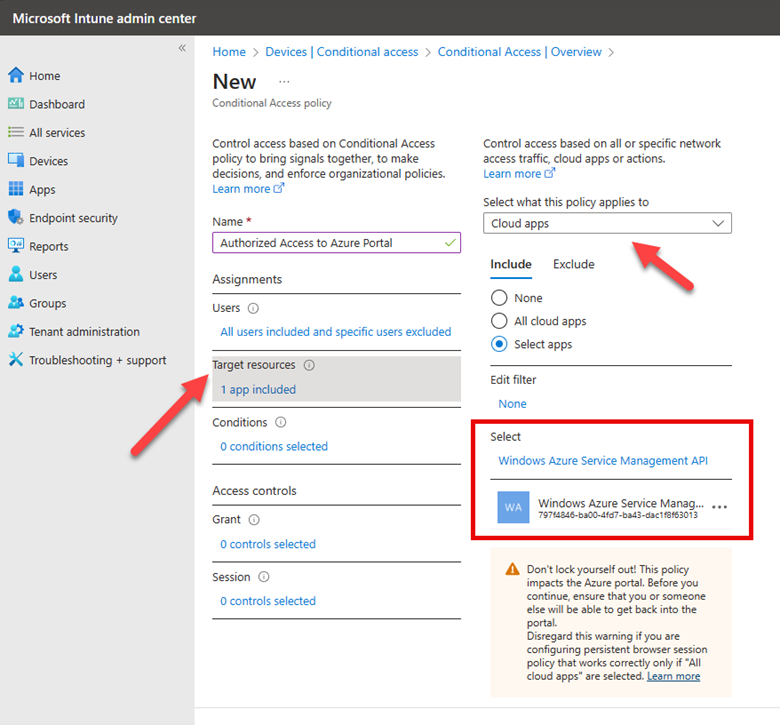
After naming the policy it is time to configure settings as shown below. Of course, in this instance we will choose Azure AD only as the Backup Directory.
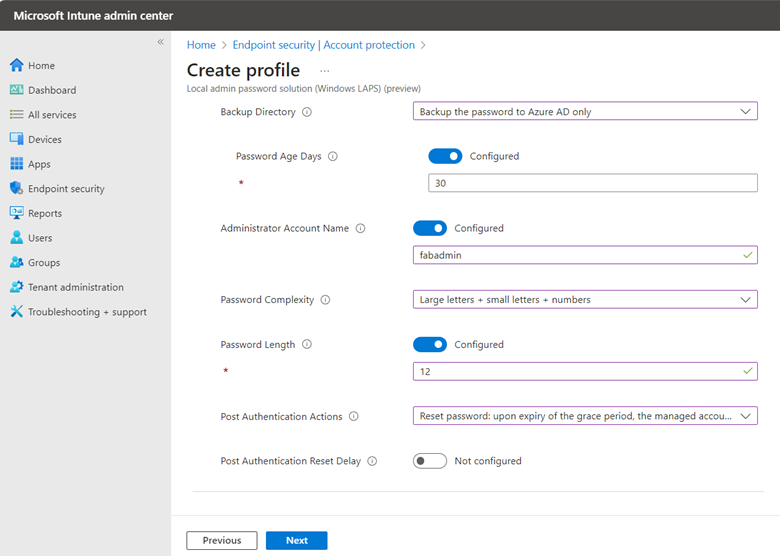
For the Administrator Account Name, I chose a custom account called fabadmin. If you are using Windows LAPS to manage any custom local administrator account, you must enter the name of that account here. You can leave this field blank if you are configuring LAPS for the built-in administrator, even if you have changed the name from its default name.
For Password Complexity there are four options:
- Large letters
- Large letters + small letters
- Large letters + small letters + numbers
- Large letters + small letters + numbers + special characters
Note that four options are the default if you don’t select an option.
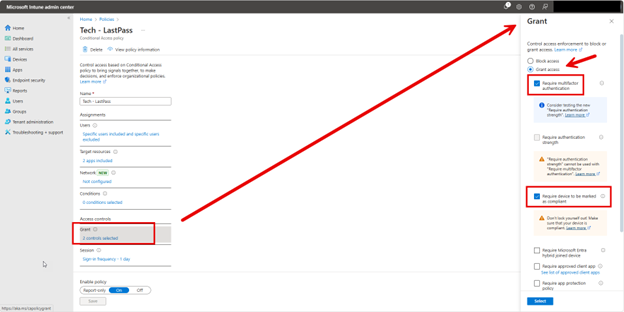
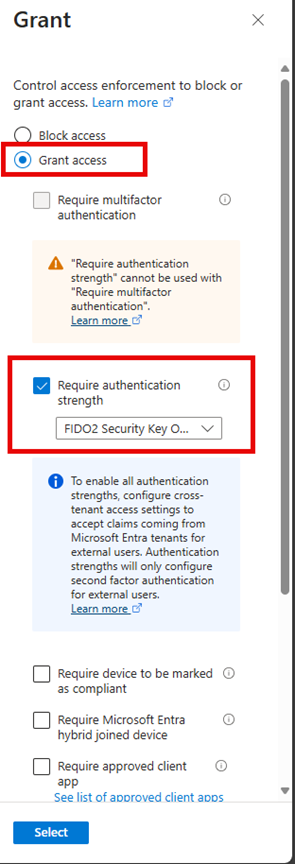
Post Authentication Actions is used to specify the actions to take upon expiration of the configured grace period which is 12 days in this instance. There are three options here.
- Reset password: upon expiry of the grace period, the managed account password will be reset.
- Reset the password and logoff the managed account: upon expiry of the grace period, the managed account password will be reset and any interactive logon sessions using the managed account will be terminated. (Default behavior)
- Reset the password and reboot: upon expiry of the grace period, the managed account password will be reset, and the managed device will be immediately rebooted.
- Not configured.
If no selection is made, the setting will default to the logoff option.
Post Authentication Reset Delay Sets the delay in hours before the previous actions above is executed. The default is 24 hours which is also the maximum.
With your settings configured, assign relevant scopes, and deploy the rule to the Azure Ad group you want to manage with this policy. In my next blog I will talk about how to retrieve the password from Azure and how to audit LAPS retrieval.