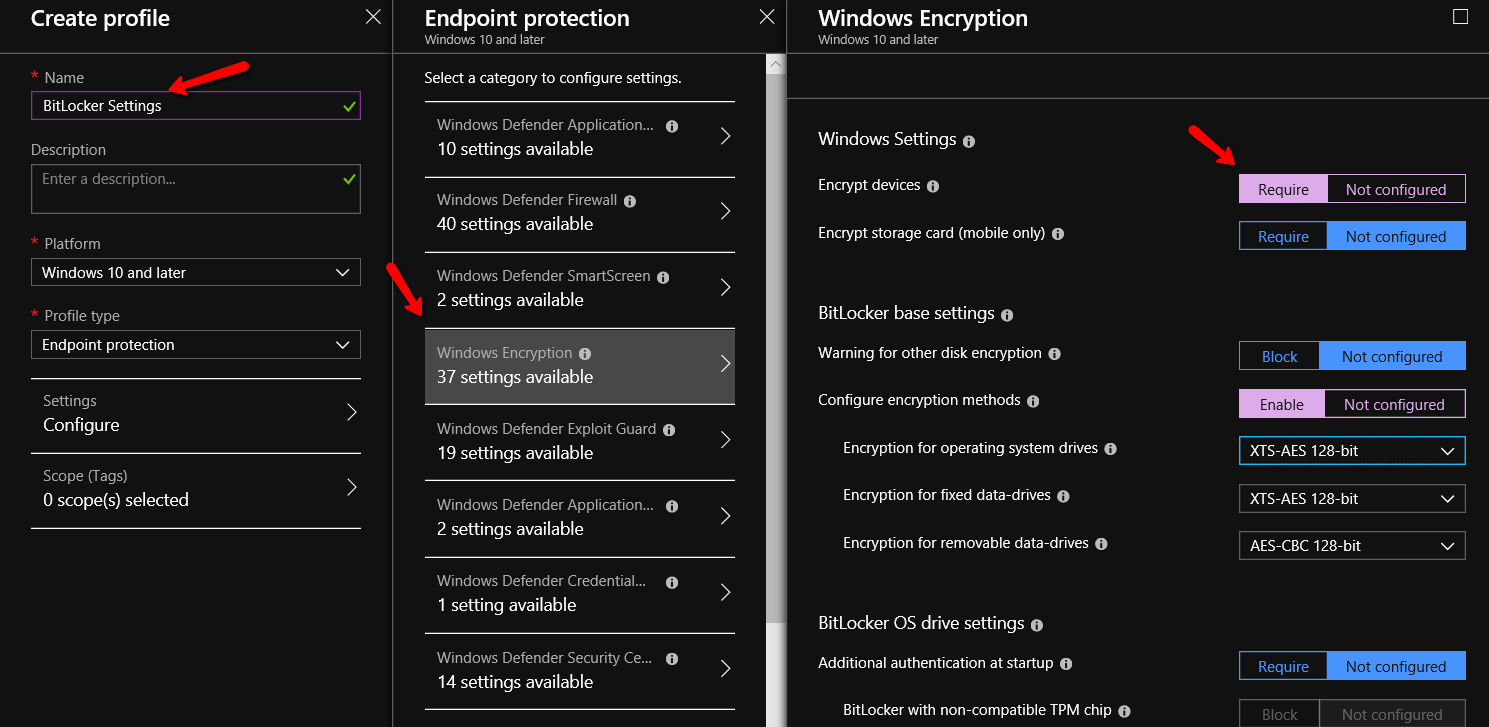
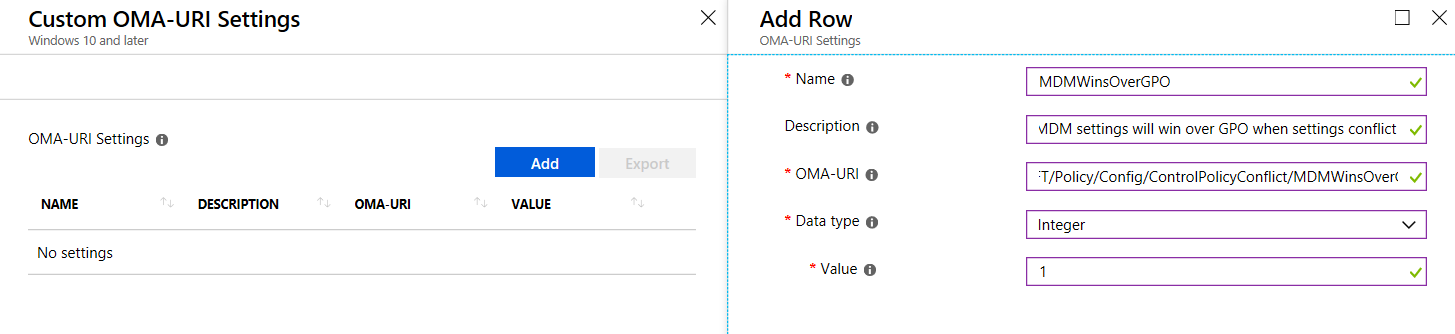
Microsoft Endpoint Manager and Group Policy (or what I learned at Ignite 2019)
So Ignite 2019 is behind me (and us). And I wanted to give you some of my insights into what I took away (and how I participated.)
First, Microsoft is such a huge company that this year, with all the new stuff coming out (or changes to existing products) Microsoft put out a “book of news” which is a giant PDF of all the what’s new. It’s only 85 pages. Ow ow ow ow ow.
https://news.microsoft.com/wp-content/uploads/prod/sites/563/2019/11/Ignite-2019-Book-of-News-2.pdf
That being said, I’m going to cut to the chase for what I specialize in and think most about: Windows desktop management with Group Policy and MDM.
It starts off with this announcement: Microsoft SCCM and Microsoft Intune are now under a unified product umbrella called “MEM”: Microsoft Endpoint Manager. With this, naturally, there are going to be some questions:
- What does this mean for you?
- What does this mean for on-prem (SCCM and Group Policy) worlds?
- And what does this mean for existing SCCM and existing Intune customers?
Let me try to answer that in this blog. To do that, I want to quote Microsoft leadership (VP Brad Anderson) in his kickoff address:
"Modern management does not mean cloud-only. It does not mean a migration away from ConfigMgr, or a migration to Intune. Modern management puts the cloud intelligence that comes from organizations like Microsoft to work to automate tasks, prioritize your efforts, connect the IT and Security teams, and continually improve the user experience. We do believe the destination many organizations will arrive at over time will be a cloud-only management solution with Intune and Microsoft 365 at the center, but we want to enable you to take advantage of our cloud capabilities incrementally at your own pace – without replacing infrastructure as some of you may not be ready for a full cloud migration. This enables you to get cloud value along with your on-prem deployments, on the road to full cloud/modern transformation."
Let’s break this down (my words interpreting Brad; this is not Brad himself):
- “Hey Microsoft Customer”: what you’re doing now is okay. (SCCM & Group Policy still has a place, works as expected and continues to work for desktops, onprem servers, VDI etc.)
- “Hey Microsoft Customer”: Cloud is great. If you’re ready for it, great. When you start to use it you’ll get added cloud benefits.
- “Hey Microsoft Customer”: You don’t have to DUMP AND JUMP what you’ve built to cloudland. We think you’ll get there eventually.
- "Hey Microsoft Customer": The tools you use today, like Group Policy and SCCM, aren’t going away. In fact, they can't go away.
This is ALL good news. For all scenarios and customers: What you’re doing isn’t going away, but there’s options for you if you want to take advantage of the cloud. Indeed, the newest philosophy and guidance (which I took away from multiple sessions) appears to be:
- Keep your PCs / servers / Citrix/ VDI / everything in Group Policy / SCCM land for now.
- Cloud attach / Hybrid Azure AD join to gain some cloud attached features, increased security, reporting, and insights.
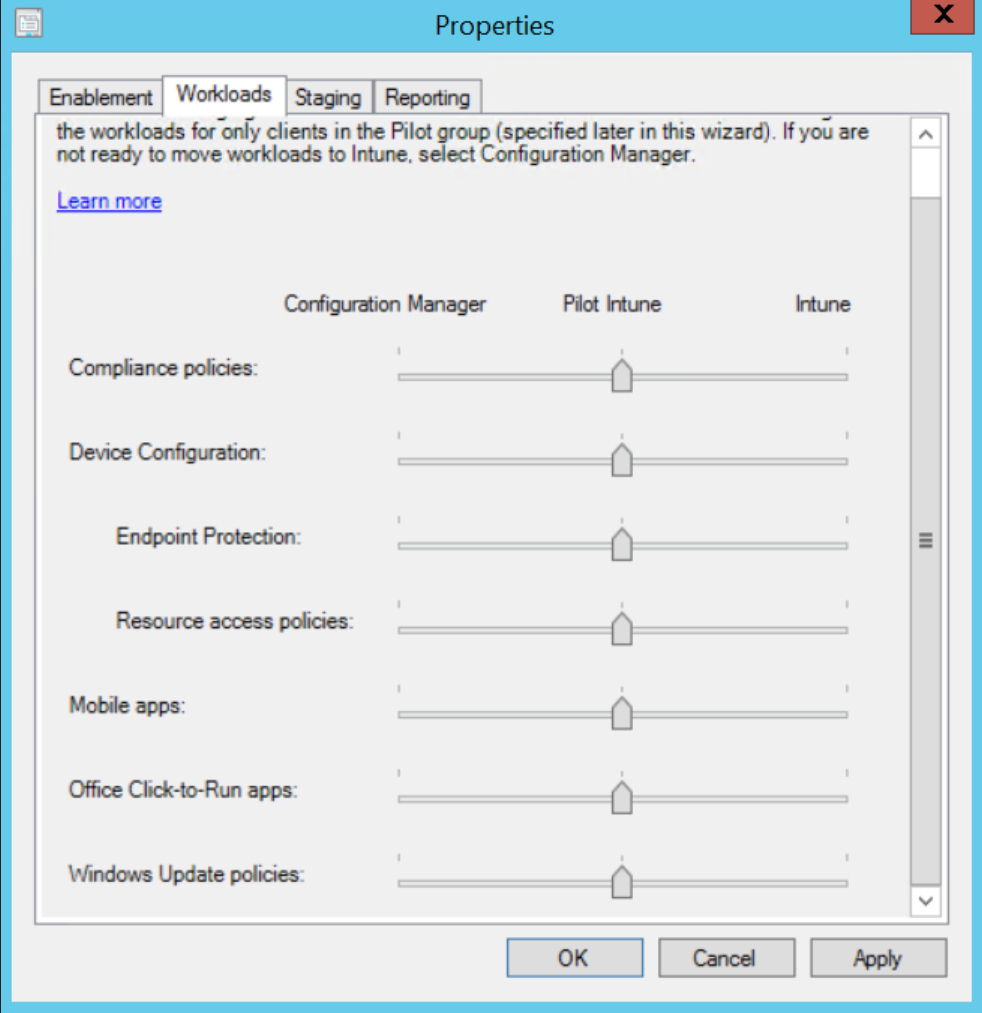
- From a policy (and workload) management perspective: pick one. Group Policy or MDM or SCCM for the particular job.
On stage, at least two Microsoft-led sessions referenced my new MDM book (whoa! Thanks Microsoft friends!) and expressed (my sentiment) that trying to untangle a machine with both Group Policy **AND** MDM settings on the same box is a difficult problem. And one that should be avoided.
In Ghostbuster’s parlance:
“Don’t cross the streams…it would be bad. Try to imagine all life as you know it stopping instantaneously and every molecule in your body exploding at the speed of light.”
(Full scene here: https://www.youtube.com/watch?v=wyKQe_i9yyo )
Maybe not that bad, but.. in that ballpark.
So what does this mean for you? The “take away” advice I felt I got was: once you’re settled and have the cloud / Azure/ MDM (Intune or other) reasonably handled, then NEW deployments of Windows 10 can be cloud only … from a management and policy perspective.
So how can Group Policy, Azure, MDM and SCCM be used at the same time… but take on different (non-conflicting) roles? Here’s an example:
- Roll out a machine using Azure and Autopilot and perform a hybrid Azure AD join.
- Machine gets on-prem Group Policy setting for Windows-y and security things.
- Machine gets software deployment settings from MDM.
- Machine gets patching and updates from SCCM.
Again: That’s just one way to slice it. There are surely others.
So… the message to customers from Microsoft would now be (again, my interpretation; not one person directly.):
- Get ready for, understand, and use the cloud when you can.
- Attach your on-prem universe to the cloud for cloud-attached benefits.
- Yes, we realize utilizing the cloud could actually be a long, long time before you get there and are comfortable. Perhaps many years.
- Once you’re there in cloudland, we recommend new PC deployments can be in the cloud.
- Even then, we realize Group Policy will always be used for some circumstances, and we’re cool with that. (So, once again, Group Policy isn’t somehow ‘going away.’). Indeed, even today Windows Virtual Desktop requires on-prem Active Directory and Group Policy even though the WVD machines are in Azure / the cloud. (You can see my walkthrough and gettings started with WVD here if you want to give it a try!)
That being said, Microsoft is trying to make it easier for you to take your existing Group Policy settings and see if it’s possible to use them in MDM-land if you choose to do it. Already, they have the MMAT tool which can analyze your existing Group Policy Objects (or an endpoint) and give you a report on what will, and what won’t transition to MDM-land. .. and I talk about it in my MDM book, chapter 5. Get your signed copy now.?)
What was announced this week with regards to Group Policy and Intune are two items:
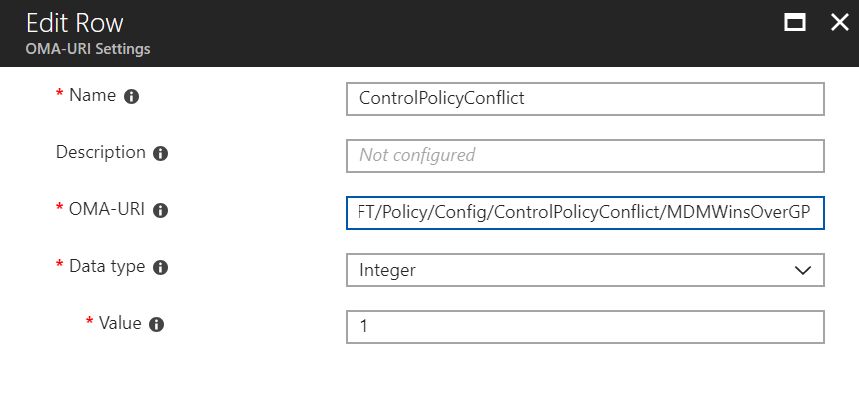
1. Microsoft is going to ship a “CSE TOOL” which customers can add-into Windows 10, when a machine is born, or after the fact. This CSE Tool will then be able accept some directives from your MDM service (like Intune or others) and poke at SOME Microsoft Group Policy CSEs to instantiate some Group Policy functions. The first items that Microsoft is tackling are:
- Drive maps.
- NON “Microsoft policies keys” in Registry (think unusual ADM / ADMX files).
- Auditing.
These items are interesting if the idea is to stop using Group Policy for these items and then use MDM instead. (Again, don’t cross the streams.) What is interesting though is that (again) the MDM provider will have to call this CSE tool, which then actually performs the work in the Group Policy CSE. Which, once again, friends … means that Group Policy cannot die. This essentially guarantees it.
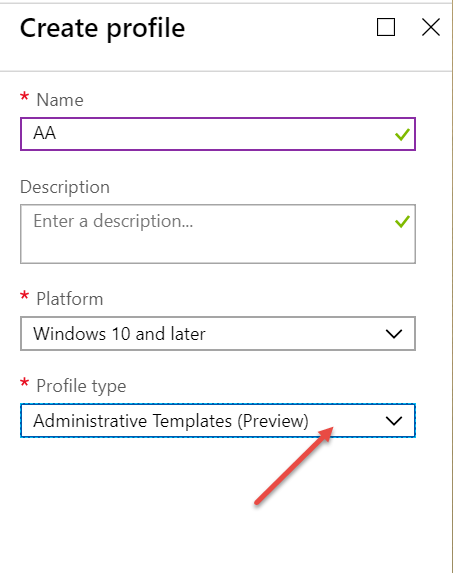
2. Microsoft also demonstrated a future feature in Intune, which is SIMILAR in practice to MMAT I mentioned above. The gist is that you can show Intune a GPO backup which Intune can now analyze. Then if the settings in the GPO exist, an Intune profile will be made (with the equivalent settings in Intune land.)
That being said, as was repeated several times across multiple sessions: If you’re going to attempt a transition from Group Policy to MDM, don’t “lift and shift” over your settings without making proper decisions to keep or kill a setting.
Then, additionally, if you’ve now lifted and shifted Group Policy to MDM… here we go again… don’t cross the streams.
With any tool which makes things easier, use it wisely with a heap of planning to know what your destination should look like. Don’t just use the tool (any tool) because it’s there.
My little inner fear here is that many companies won’t heed this advice, and very quickly be in the same place like “I’ve got too many MDM profiles where I don’t know what they’re doing !!” as they already do in the “I’ve got too many GPOs where I don’t know what they’re doing!!” place they are right now.
So in summary, here’s what I learned at Ignite 2019:
- Intune and SCCM are now under one umbrella: Microsoft Endpoint Manager. Indeed, if you’re an existing SCCM customer, you now automatically get Windows Intune licenses for managing Windows devices via Intune. Note that this doesn’t mean you magically get, say, iOS or Mac or other non-Windows PC licenses. Also note this requires an Azure Active Directory P1 (at least) subscription for your organization.
- It’s okay to be on-prem, and it’s okay to be cloud. Cloud is a destination, but destinations take a long time to manifest.
- Microsoft is increasing their tooling for Group Policy understanding and to take on some better Group Policy to MDM migration scenarios for those who feel they are ready to go there.
- (once again) Group Policy isn’t dead.
So, take a deep breath. You’re doing fine. If you’ve got no toes in, or one toe in, or nine toes into the cloud… you’re doing fine. And, yes, I realize, you cannot put toes into cloud, but just go with me here.
I hope this blog entry helps you out and you’ll share it with your friends, your boss, and anyone else who wants to learn what’s new in management this year from Ignite 2019.
PS: Here’s some pictures of me at Ignite:
- First in the Microsoft Endpoint manager booth (https://twitter.com/jeremymoskowitz/status/1192204319745024005
- Second at the bookstore with my Group Policy and MDM books https://twitter.com/jeremymoskowitz/status/1191776777452032002
- Third, petting a therapy animal who is there for some down time with the geeks https://twitter.com/jeremymoskowitz/status/1191782442354532353
Ignite 2019 was really bananas, and it was awesome seeing many of you in person !