RSAT for Windows 10
RSAT is the “Remote Server Admin Tools.”
It’s like the old “Adminpak.MSI”.. but.. it’s got a new name.
And its out for Windows 10 now. Here’s the link !
http://www.microsoft.com/en-us/download/details.aspx?id=45520
Enjoy !

RSAT is the “Remote Server Admin Tools.”
It’s like the old “Adminpak.MSI”.. but.. it’s got a new name.
And its out for Windows 10 now. Here’s the link !
http://www.microsoft.com/en-us/download/details.aspx?id=45520
Enjoy !
Here’s an email I got and my response. The names have been changed to protect the innocent.
—
Hi Jeremy,
Let me briefly introduce myself. I’m working as a system administrator in a public institution. I would say that I’m relatively new in the field (just 3 years). Recently I encountered a problem at my workplace that bothered me a lot. I was confused and therefore need some suggestions/advice. Maybe you can help to clear the confusion.
By the way, I also have a copy of your book, “Group Policy: Fundamentals, Security, and the Managed Desktop” and I like reading it. It’s very informative.
At my workplace, we have:
– One Domain Controller that running Server 2008.
– Our client environment consists of Windows 7 and Windows 8.
In order to manage the new features/setting in Windows 8 through GPMC, I decided to:
– Use Windows 8 Management Station with RSAT installed.
– I also created the Central Store with the ADMX for Win 8 and Server 2012.
Controlling the settings from Win 8 management station was working fine for me.
I didn’t have any problems with the group policy and the settings were applied to the client machines as planned.
However, my boss doesn’t agree with the use of a Windows 8 RSAT / Management Station.
According to him RSAT is compromising the security and defeating the purpose of the Domain Controller.
He argues:
-That RSAT doesn’t have a record of who logged in to the DC. He’s saying that when someone logs in to DC, either using Remote Desktop Connection or physically present in front of the server, DC authenticates and has a record.
-Second, he argues that the best way to manage or control settings of Windows 8 machines is by using server 2012 and not using a Win 8 Management Station with RSAT installed. He thinks that this is vulnerable and Win 8 is never meant to serve as a server in managing client machines, and that everything needs to be done from the server instead of Management Station.
I was very confused with his opinions regarding RSAT.
Is he right that RSAT is compromising the security and defeating the purpose of DC, and that WIN 8 is never meant to be used to edit the group policy? Please advice. Looking forward to hearing from you.
Thanks, – Jake
—
So, Jake … your boss is partially right and partially wrong.
1. All Windows systems have auditing. SO if you use a Windows 8 machine and log on, you can track that, and “Forward the events” somewhere for an audit record.
2. Note: DCs do specifically log to the event log WHO logged in.
3. That being said, when it comes to logging GPO creation, it also does that anyway.
4. In no case, ever.. does it tell you *WHAT* was changed/done inside a GPO. That data doesn’t get captured.
5. There is no “intrinsic security risk” just by using a Windows 8 management station with RSAT vs. using a DC to make a GPO. It’s what I recommend.
6. You noted you only had ONE DC .. that’s .. um.. bad. If you had a problem or it went down, no one could log on. Consider having more than one DC.
Hope these notes help you out.
-Jeremy Moskowitz, Enterprise Mobility MVP
The Internet is full of free Active Directory tools out there. Some are worthwhile, some aren't.
I kind of like it when companies provide free tools. Of course, they do it to increase brand awareness for their pay tools.
But thats okay by me if the tools work and do some magic that would be hard for me to do on my own, without looking up commands, functions, and tons of documentation with lots of steps.
My friends at ManageEngine offer a package suite of free AD tools called ADManager Plus. Most of these tools center around the objective of simplicity. They take cumbersome or annoying AD tasks and make them simple and straightforward. All of the tools in ADManager Plus are based on Powershell cmdlets. This requires PowerShell to be installed on the machine where these tools are run. Most of the tools list the PowerShell cmdlet the tool is based on if you prefer to simply use PowerShell. The entire suite installs in less than a minute and very intuitive to use right from the get-go.
Lets take a look at three tools in their set. The set can be downloaded here.
Note: It should be noted that ManageEngine does advertise on GPanswers.com, but this is an independent and hopefully un-biased review. Besides, these are free tools. How can you go wrong?
The first free tool is their Domain Controller Roles Reporter. We all know the traditional but complex process of opening up three separate AD tools (AD Users and Computers, AD Schema and AD Domains and Trust) to figure out which DCs host the five operation master roles as well as which servers act as global catalog servers. Instead of utilizing multiple tools, Domain Controller Roles Reporter lists each DC in your AD structure as well as their assigned roles; all in one easy to view list. Imagine obtaining all of your DC roles in less than a minute. That is easily obtainable with this tool. Although my demonstration domain consists of only one domain controller, you can get the drift of this easy-to-use utility in the screen shot below.
Another great simplifying tool is their AD Replication Manager.
Any domain administrator knows the rigmarole of using AD Sites and Services to replicate designated DCs within their domain structure. Again, ManageEngine offers you a simple design in this utility. With the single click of a mouse, one can replicate all of the DCs within your domain or even forest. It will even allow you the ability to replicate any two DCs of your choosing whether they are assigned as AD Connectors or not. Each of these capabilities is illustrated in the screenshost below.
The Last Logon Reporter may be the standout of the bunch.
Every administrator has been asked at some point within an organization about when the last time a particular employee logged onto the network.
In an AD environment consisting of many domain controllers, this can be a time consuming task. Just trying to find which domain controller the user last logged onto is a time consuming enough. Once again, ManageEngine provides a one stop utility that allows you the ability to retrieve the information you need quickly and efficiently. Below is a demonstration of the simple two-step process that provides you with the last logon time for any user in your domain.
How many times have you attempted to use the Windows RDP client to connect to a remote server, only to be informed that the server has exceeded the maximum number of allowed connections. You then had to access the terminal services manager for that server from another machine in order to log the sessions off.
ManageEngine's Terminal Session Manager will search your network for remote sessions and list them all, again in one viewable list. You can then obtain information concerning any of these sessions and either disconnect them or log them off. This two-step process is outlined below.
Believe it or not, we've barely scratched the surface in covering all of the great applications that make up the ADManager Plus suite.
Other tools include a Password Policy Manager, a Local User Management utility and a DC Monitoring utility. Other applications help identify AD object name duplicates, empty passwords and we still haven't covered them all. ADManage Plus may be free, but it offers definite value to the network administrator today who will find at least one of these tools a fantastic addition to their network administrator tool belt.
Hope you like the tool roundup !
This blog entry is two tips in one. Click to find out why. Inside you'll learn about the RSAT tools and also where the GPPEs can be downloaded using Microsoft Update.
Remember the ADMINPAK? It's not available on Vista, but the all-new released-today RSAT tools are. RSAT stands for "Remote Server Administration Tools." It contains the GPMC, ADUC, and all the greatest hits.
Download the Vista + SP1 + x86 version here: ttp://tinyurl.com/3xs2o6
Download the Vista + SP1 + x64 version here: http://tinyurl.com/337gfj
PS: I'm seeing the links going up and down all day today. It's weird.
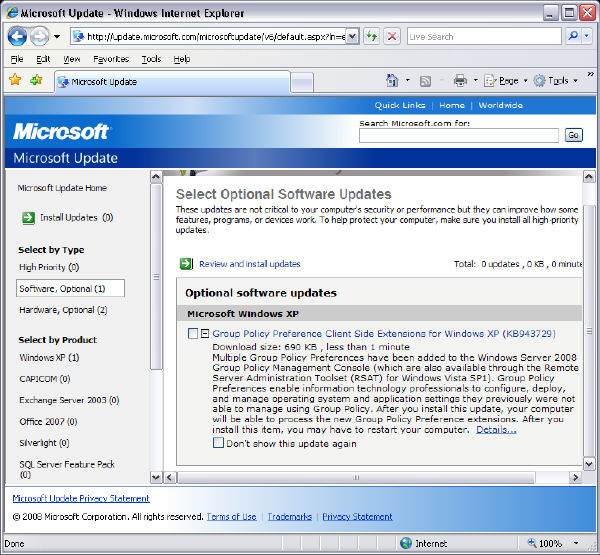
In other news, the GPPEs are available as "Optional Software updates" using Microsoft Update as seen here. Thanks to Scott Bailey for this tip !
One of the hardest jobs is figuring out which users need Admin rights, because our stinkin' applications require admin rights. Well, that's the business of BeyondTrust. And today, they came out with a (free) tool to help you determine which applications require what admin rights to run. Sure, the idea is that you'll have an "A-ha" moment and realize that their (pay) tool (which is quite good) is the best way to keep the user's rights LOW, but elevate the rights of the application. To check out the free auditor tool they came out with today, head on over here.
So the other day I posted about a Softgrid to MSI repackaging tool. Great! Except it doesn't work with the existing Softgrid client. (Boo.) But the new client is now out! (Yay!)
http://support.microsoft.com/kb/941408
Why they didn't come out at the same time is a bit of a mystery. But.. That's the breaks sometimes. Anyway.. Enjoy Softgrid geeks ! (PS: I'm one of you!)
So, I can confess it. I love Microsoft Softgrid. I really do. For the uninitiated, Softgrid (newly renamed Microsoft Application Virtualization) can take an application and "stream" it from a server to your desktop. Keen-o-rific. This means you're not actually INSTALLING anything; but rather, just running it streamed. Except there was no way to "deploy" that application using GP. Until now. Enter in the Softgrid MSI "wrapper" utility (found here.)
The idea is simple: if you can wrap an existing Softgrid package into an MSI, then you can use GP (or SMS, or Landesk or anything) to maintain your deployment practices.
I haven't had a chance to try this out yet.. So, if you do, and you're a Softgrid + GP head, then shoot me an email and let me know how it went! Thanks !
PS: Thanks to GPanswers.com Shortstop Eric Johnson for bringing to my attention that this tool was FINALLY available.
Two quick notes:
Note #1:
In my testing of FullArmor/Microsoft's ADM to ADMX migrator tool, I encountered a bunch of issues. Namely, all sorts of ADM files I had hanging around wouldn't properly convert to ADMX. Actually, they WOULD convert, but then in the GPOE editor they would bomb out. So, after I reported these errors to FullArmor/Microsoft, I'm happy to say I got a great response for others in the same boat: "We've been working on a new release of ADMX Migrator and have resolved most of the issues including all of the issues raised by Jeremy. We will be feature complete in the next week and a half and expect to release beginning of October 2007. "
Note #2:
I have a new NetIQ sponsored whitepaper out called "Why GP Matters -- For Servers". Click here for that paper.
Note #3:
GPanswers.com now has a search engine. Check it out on the main page !
Vista has a whole new event log with a zillion GP events in it. Of course, details in some upcoming newsletter. For those trailblaizers though, there is a tool to help you parse those Vista logs.
The GPLogview tool was published on the Microsoft Download Center the other day:
http://go.microsoft.com/fwlink/?LinkId=75004 .
Send me an email with how it works for you.